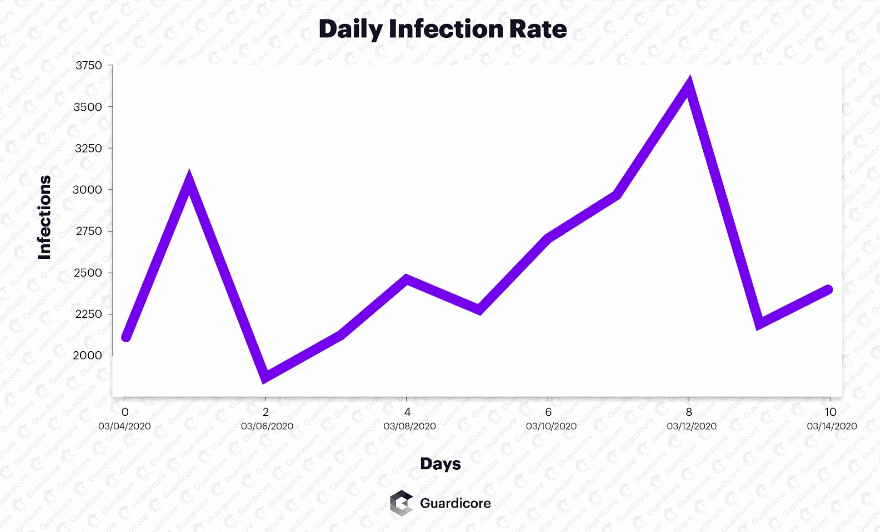
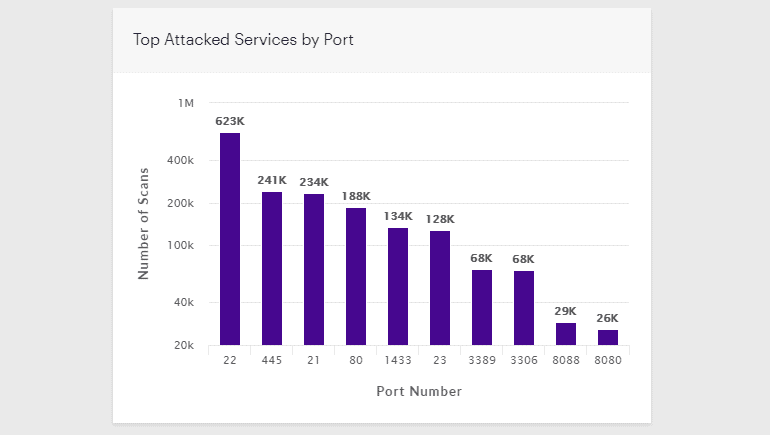
The Botnet is still active and infects approximately 3,000 new MSSQL databases every day, as defined in a study published by cybersecurity company Guardicore. Guardicore called Botnet Vollger, which has been de-facto alt-coin mined by most of today’s botnets based on its predisposition to mining the Vollger crypto-currency (VDS) alongside Monero (XMR). The brute attacks aimed at divining the MSSQL servers password have flooded the entire internet. Guardicore claims they have over 120 IPs used to launch attacks since May 2018, and most IPs are from China. Harpaz said the Botnet was continuously churning, with the Botnet losing servers and adding new servers every day. More than 60% of all secret MSSQL servers remain with the Vollgar crypto-mining malware for short periods of up to two days, depending on Guardicore. Nearly 20% of all MSSQL systems are infected for more than a week, and even longer, Harpaz states. However. This is because either Vollgar malware tends to cover itself from social security tools, or the database does not start with one. But Guardicore also states that 10 percent of all victims get reinfected with the malware. Another vital statistic is the truth. Harpaz says it typically occurs because the administrators do not correctly uninstall all malware modules, leaving the door to reinstall the malware. Guardicore has released a GitHub repository with file and backdoor accounts created by Vollgar malware on infected host systems to support victims with MSSQL administrations.