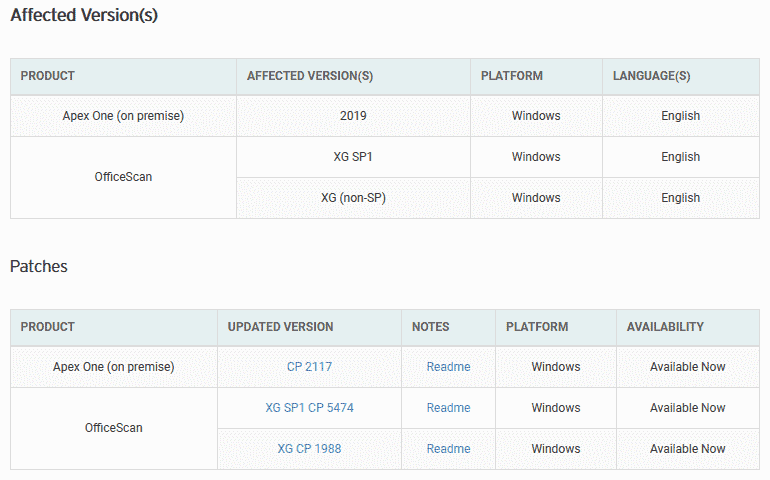
Hackers are attempting to hack two zero-days in Trend Micro antivirus software; the firm said in a security warning this week. The Japanese antivirus vendor published patches on Monday to fix two zero-day problems, along with three other similarly significant problems (though not abused in the wild). According to the warning, the two zero-day protection devices of the firm Apex One and OfficeScan XG affect the business. Trend Micro did not provide any specifics of the assaults. These two zero-day vulnerabilities are the second and third Pattern Micro antivirus vulnerabilities that have been targeted in the wild over the last year. In the summer of 2019, Chinese state-sponsored hackers used a zero-day Pattern Micro Office Search (CVE-2019-18187) to assault the Japanese electronics firm Mitsubishi Electric. It is not clear if the two zero-days revealed this week are linked to last year’s zero-day or if they are being used by the same hacker community (known as Tick). ZERO-DAY DETAILS Under the Trend Micro Safety Bulletin, the two zero-days are as follows:
- CVE-2020-8467: CVSS 9.1 (CRITICAL)-Trend Micro Apex One migration tool component and OfficeScan contains a vulnerability that could allow remote attackers to execute arbitrary code on affected installations (RCE). An unsuccessful attack includes verification by the recipient.
- CVE-2020-8468: CVSS 8.0 (HIGH)-Trend Micro Apex One and OfficeScan are impacted by a code validation escape flaw that could enable an intruder to exploit other agent-client components. An unsuccessful attack includes verification by the recipient. The only point that can be gleaned from the information above is that zero-day hacker expected to obtain legitimate credentials for the victim’s workstations, which implies that they were more definitely introduced in the post-compromise situation because hackers had already breached the company’s internal network. Two zero-days most definitely used either to uninstall protection software or to improve the rights of attackers on computers operating the two Pattern Micro antivirus software. Trend Micro attributed its analysts with the detection of two zero-day vulnerabilities and three other vulnerabilities. The organization started paying more attention to vulnerabilities in its software after Chinese hackers last year abused its antivirus in the Mitsubishi Electric Attack. Such activities resulted in last month, during February 2020, when Trend Micro revealed involved in collecting vulnerability reports in three of its main antivirus products (Apex One, OfficeScane, Deep Security) from independent researchers via its Zero-Day vulnerability acquisition program.