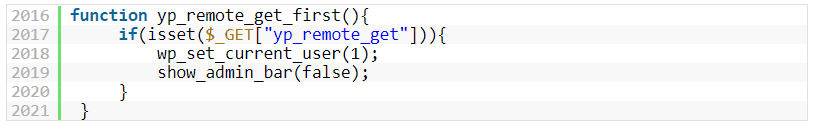
On Monday More to the point, malicious actors can potentially change both the site and home URLs with an unauthenticated SQL injection, after successfully exploiting the vulnerability. Exactly that is the case with a number of unfortunate webmasters who hacked their WordPress websites (Fix malicious redirects wordpress) because of the vulnerability of the plugin with an installation base of more than 30,000 websites, according to HERE, HERE and HERE. As per wordfence reporter: “We’re again seeing commonalities between these exploit attempts and attacks on recently discovered vulnerabilities in the Social Warfare, Easy WP SMTP and Yuzo Related Posts plugins. Exploits so far are using a malicious script hosted on a domain, hellofromhony[.]com , which resolves to 176.123.9[.]53. That IP address was used in the other attacks mentioned. We are confident that all four attack campaigns are the work of the same threat actor.” Although 30 000 websites are certainly not unnecessary, the more interesting thing about this vulnerability is that, according to the research team from Wordfence, hackers used the same threat player for a broader campaign. As explained by researchers from Wordfence: In the Yellow Pencil Visual Theme Customizer file the bug enable the attacks and this is due to the fact that the yp remote get first) (function checks whether the yp remote get request parameter is set in each page load. The plugin automatically enhances the privileges of logged-in to an administration admin for the “rest of the request,” enabling unauthenticated users to perform actions normally reserved only for website administrators when the parameter is checked out.
yp_remote_get_first() function
Fix available for download
The team behind the Yellow Pencil Customizer Visual Theme Plugin patched the problem today with a download link for the patch. We fixed the vulnerability with 7.2.0 version. We are so sorry. There an update button will appear on your WordPress panel, Click on “update” button to update the latest version. If you don’t see the update button there, delete the plugin and update the plugin manually. Please follow these steps to update the plugin manually: Fix available for download WaspThemes, the developers of the plugin, also recognizes there are some “WordPress websites that are affected by a hack attack.” First Method Restore the WordPress database to backup. This is the safest and quick method. Please contact your server provider, they will help you to backup your database. Second Method: These websites are caused by a security issue in the visitor’s visual tool and provide two procedures for their fixing.