Matten Nelson and Vasily Kravets, security scientists, both lately found the same vulnerability in commonly used Steam Client software and said that Valve would not fix it because its vulnerability reporting program is “out of scope.”
Nelson told the vulnerability would not be fixed After this huge outcry, Valve altered her mind and published a correction. Unfortunately, however, there is still another likewise reported vulnerability. You may use the following free web scanning tool to know the issue directly.
Local privilege escalation fix Valve.
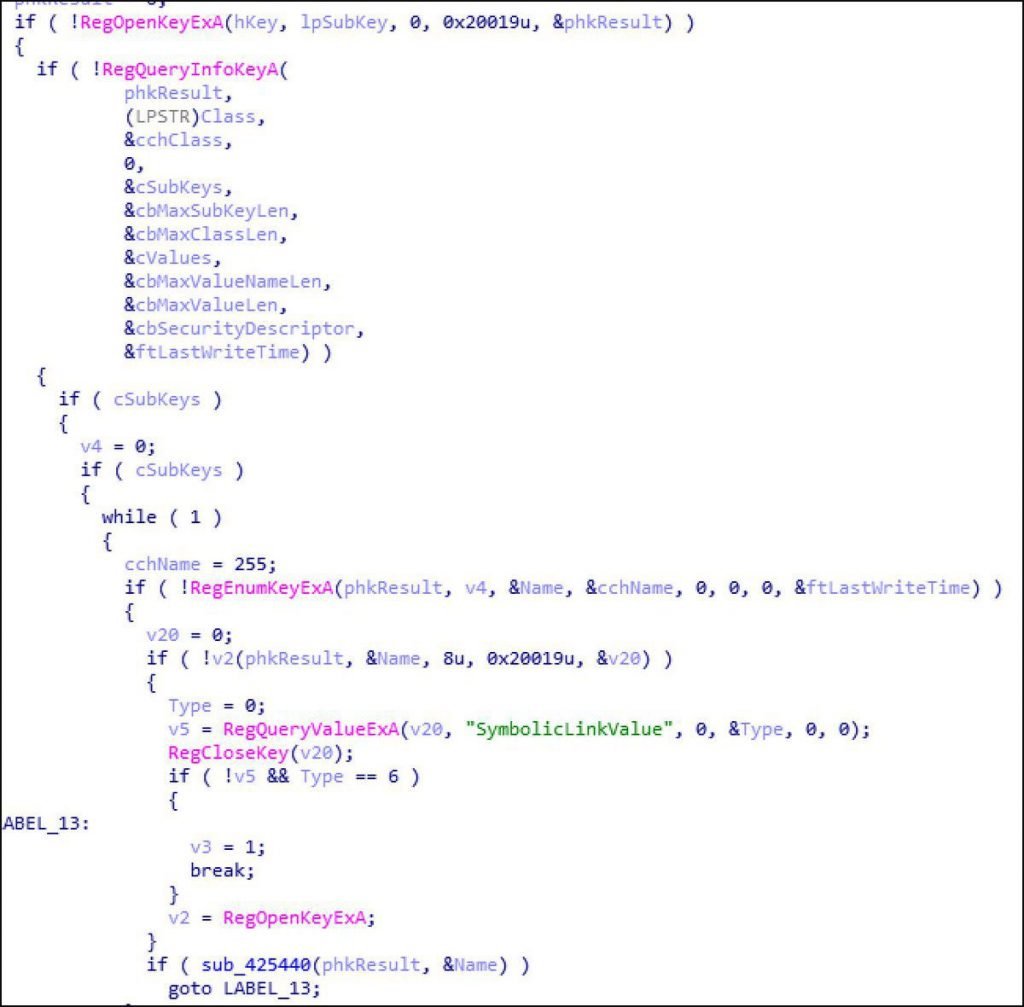
The “Steam Client Servicing” windows service gave the group “USERS” complete authorization on any subkey under the HKLM\Software\Wow6432Node\Valve\Steam\Apps Registry Key after rebooting. The vulnerability was lately revealed. With this understanding in hand, the scientists found that they could connect another key that they had no authorization under this registry key. When the Steam Client Service is restarted, the service gives complete approval for the link and thus allows scientists to use any other key within the Registry. This could then enable them to increase the privileges of any program, including malware, they want on their computer. The Steam Client Beta Valve did so by using the RegQueryValueExA feature in order to solve this, the HKLM\Software\Wow6432Node\Valve\Steam\Apps Registry key would be checked.
Check if subkey is a symbolic link When the RegQueryValueExA feature returned that the particular subkey was actually a link or REG LINK, the feature would break out and not give a full approval to the “USER” group of the key.
Fix is not enough.
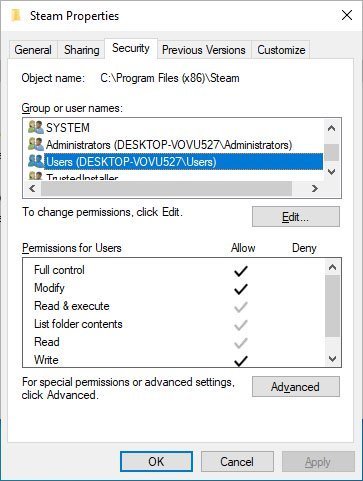
While Valve may have fixed this one vulnerability in its “Steam Client Service,” scientists are still saying that there is a huge vagueness that has long been reported and that attackers and malware still have to use to increase their rights. Vulnerability investigator and co-founderof 0Patch Mitja Kolsek have informed that the “Steam Client Service” can still be used to increase user privileges through the DLL deprivation. This vulnerability exists because a complete Steam installation folder at C:\Program Files (x86)\Steam has been granted full approval to the “USERS” group. This implies that an attacker can substitute the DLLs in this folder with a malicious copy that provides the attacker administrative access to the computer when a high-process or a service is introduced.
USERS group has Full permissions This bug is also not new. Nelson said that this problem was present, but not solved, for a while. “Yes, being completely open is an awful issue which has long been present. You try to validate the signature of these files but I doubt its sufficient.” This issue was actually notified in 2015, given the CVE ID of CVE-2015-7985, and has not been resolved until this day. “The weak default permissions of the steam Microsoft Windows client software allow read and write access to a Windows User group for the install folder have been identified, including Steam.exe that is run upon user login.”
Complete permissions for self-updates are reportedly required.
These permissions are supposed to[ 1] allow Steam customer software to update themselves and other games. When we asked Kotsek why Steam needed such permissions, rather than just an update procedure that required higher permissions, we received the following information: “There is NO valid reason for the privileged service to have executable modules that can be modified by ordinary consumers.” At the moment of this publication, we did not hear.