A post from the owner of SocialEngineered.net on Thursday announced the violation of the forum via a vulnerability of MyBB forum software. The last major MyBB vulnerability and the technical details were published on 11 June. Successful bug use-a saved cross-site scripting (XSS) and file writing, results in remote code execution and complete take-over of the target site. Although MyBB had pushed a patched version a day ago, websites typically are slow to install security fixes to allow attackers to scan the web for the targets and hack them.
Data shared on forums that crack
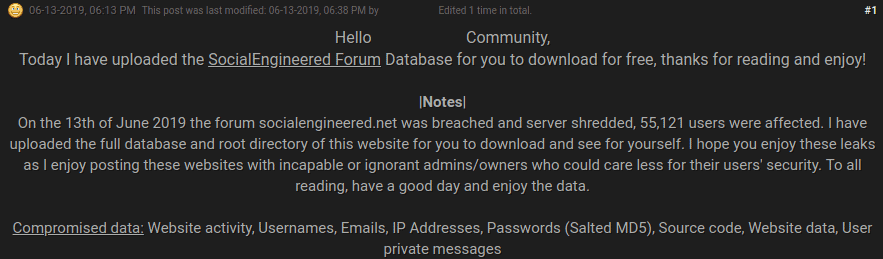
SocialEngineered.net data were dumped at a hacker forum on 13 June. The information leakers indicated that “the full database and root directory of this website has been downloaded.” The dump affects 55,121 social engineering users and includes their usernames, the passwords stored as salt MD5 hashes, email addresses, IP addresses and privacy.
The hacker seemed to be able to get much more than this, however, since a post on the rival forum informed that the leak included the source code, data and activity of the website. HaveBeenPwned added the new database to its collection and on Sunday informed that 89,000 unique email addresses were provided by the 55,000 users of the Forum to confirm the initial details. The same database was sent to another hacker forum on Friday, where several members shared positive reactions on its availability.
After the hack, SocialEngineered moved to the XenForo forum platform to prevent a future similar incident. The owner requested that the login passwords be changed from the member side immediately. As new vulnerabilities become available, hackers will quickly seize them and look for potential targets. This incident is a clear example of how quickly attackers can hit because the threat actor only required two days to compromise a website and publish details.