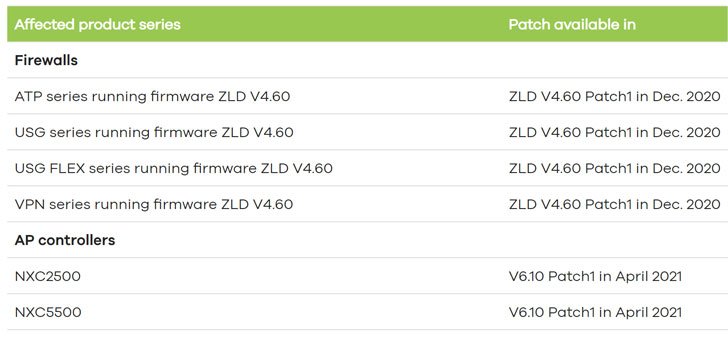
The fault, monitored as CVE-2020-29583 (CVSS score 7.8), affects version 4.60 of Zyxel’s wide range of devices, including Unified Security Gateway (USG), USG FLEX, ATP, and VPN firewall items. The vulnerability to Zyxel was identified by EYE researcher Niels Teusink on November 29, after which the company released a firmware patch (ZLD V4.60 Patch1) on December 18th. The undocumented account (“zyfwp”) arrives with an unchanged password (“PrOw!aN fXp”) according to the advisory released by Zyxel, which is not only kept in plaintext but may even be used by a hostile third party to login with admin rights to the SSH server or web interface. In order to provide automatic firmware updates to linked access points via FTP, Zyxel said the hardcoded credentials were placed in place. Noting that about 10% of 1000 computers run the affected firmware version in the Netherlands, Teusink said the relative ease of manipulation of the bug renders it a crucial vulnerability. “As the ‘zyfwp’ user has admin privileges, this is a serious vulnerability,” Teusink said in a write-up. “An attacker could completely compromise the confidentiality, integrity and availability of the device.” “Someone could for example change firewall settings to allow or block certain traffic. They could also intercept traffic or create VPN accounts to gain access to the network behind the device. Combined with a vulnerability like Zerologon this could be devastating to small and medium businesses.”
It is also anticipated that the Taiwanese organisation will resolve the problem with a V6.10 Patch1 in its access point (AP) controllers that will be issued in April 2021. To mitigate the risk associated with the bug, it is strongly recommended that users instal the requisite firmware updates.