The hackers found the databank, which was completely unprotected, quickly and without any authentication, anybody with the right link could access its contents. The owner of the database is a Mexican librarian named Librería Porrúa, and the following information is included:
invoices with purchase details shopping cart ID payment card info (hashed) activation codes and tokens full names email addresses phone numbers dates of birth discount codes
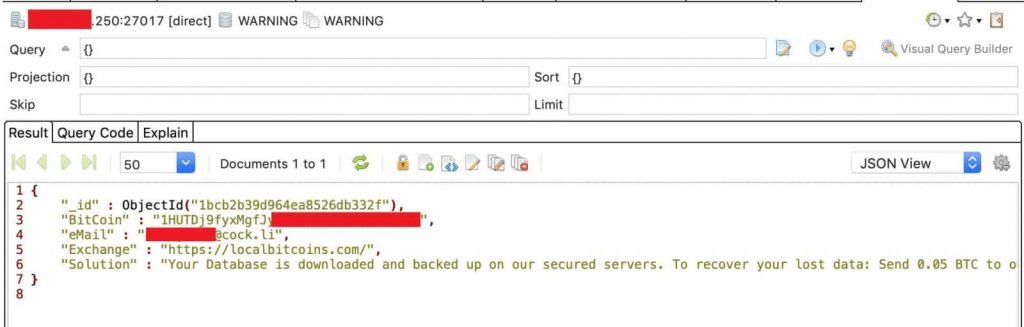
On July 15, security investigator Bob Diachenko discovered the MongoDB instance one day after the Shodan search engine had indexed it. Three days later, the database contents were washed away and a ransom request took place. The cyber-criminals said that the information was backed up and requested 0.05 BTC (approximately $500) to return it.
Hackers could manage content with full privileges without access protection to stop them. This means that, like an authorized admin with full management rights, they can connect and manage it remotely. Diachenko says. Incidents involving cyber criminals wiping databases and demanding a ransom have occurred since at least 2016 and have continued until 2017, 2018 and 2019. Tens of thousands of MongoDB databases have been deleted because admins have opened them on the internet. It is important to note that while paying for the ransom the data can be returned, it does not guarantee that hackers do not maintain a copy and resell it. In addition, the attackers often do not even bother to copy the information and simply replace it with a ransom note. It is not difficult to avoid such incidents, as long as MongoDB admins allow password protection for databases facing the internet at the very least. MongoDB has published a set of security checks that provide better protection for MongoDB facilities for more comprehensive measures.