Phishing is used by crooks to trick prospective victims through social engineering methods to pass on delicate data via their fraudulent websites or to produce malicious content through e-mails that are sent by someone they know or by a lawful organisation. While using false resumes and various other document forms is a very prevalent trick abused by cyber criminals carrying out malicious campaigns, Cofense scientists also provides a variety of anti-analysis techniques to camouflate infection vectors that are targeted at windows users by the Remote Administration Tool (RAT) in Quasar. Quasar RAT, which was created in C #, is a well-known open source RAT and used by a variety of hacking organizations, including APT33, APT10, Dropping Elephant, Stone Panda and The Gorgon Group[1, 2, 3, 4, 5]. Quasar has the capacity to open remote desktop links, log the victim’s keystrokes, steal their passwords, collect screenshots and record webcams, download and disploy files, and manage procedures on infected makers.
Phishing email sample
Delivery and infection Process
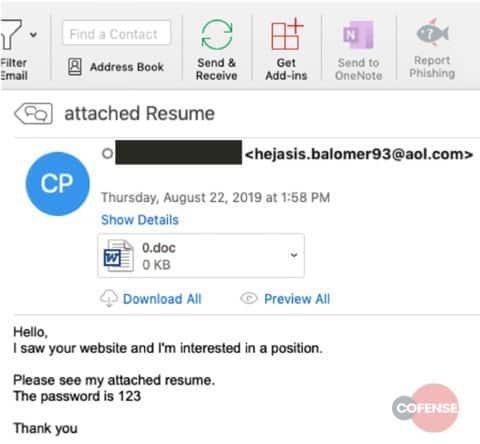
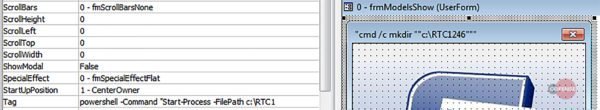
The malspam campaign identified by Cofense distributes the Quasar RAT payload using the password-protected false resumé from Microsoft Word document and also “uses counter detection measures to reach the end user.” Once the prospective victims enter the’ 123′ password, the fake resume document asks for activated macros. However, in this situation, the macros are also equipped with a tiny twist as base64 encoded waste code intended to analyze crashes. “If those strings are not decoded or the process decoding them has enough resources allocated, the resulting content still lacks the all-important payload URL,” found Cofense. “Instead, partial strings and filler text give some semblance of legitimacy.” In fact, the campaign operators have disguised payload URLs and other similar information for the infection to propagate in the metadata of other embedded objects and images. “If the macro is successfully run, it will display a series of images claiming to be loading content while repeatedly adding a garbage string to the document contents,” also found the Cofense researchers. “It will then show an error message while downloading and running a malicious executable in the background.”
Credit: Bleeping computers At the close of the Cofense study, compromise indices (IoCs) including malware hashes and network indices such as domains used for distributing Quasar payloads are accessible.
RATs are being disseminated
In this connection, therapeutic performers have been using multiple RAT flavors to target a number of kinds of goals this year alone. In assaults against utilities only last week, adwind (also known as jRAT, AlienSpy, JSocket and Sockrat) was used. In August too, attackers used a combination of fresh backdoor and RAT malware called BalkanDoor and BalkanRAT to target a number of Balkan organizations, as discovered by scientists in ESET. A new web-based attacks kit called Lord EK was also discovered in early August as part of the malvertising chain using the PopCash ad network in order to drop an original njRAT payload following abuse of an Adobe Flash usage-after-free vulnerability. Threat performers also used a fresh RAT malware called LookBack from scientists from the ProofPoint Threat Insight Team, that was supplied in a late July spear-phishing campaign targeting three U.S. companies in the public service sector. Back in June, Microsoft also released an warning of an active spam campaign to infect Korean objectives through malicious XLS attachments with FlawedAmmyyy RAT malware payloads. Cofense’s study team found another phishing campaign earlier this month to distribute a new malware called the WSH RAT, which deliberately targets clients of business banking with their data stealing and keylogging skills.