These devices are susceptible to a fresh set of vulnerabilities called USBAnywhere which influence Supermicro motherboards ‘ baseboard management (BMC) firmware. Patches are accessible to solve USB vulnerabilities, but Supermicro and Security Specialists are recommending that BMC internet management interfaces be restricted as a precaution and best practice for the sector.
What are BMCs?
BMCs are part of the IPMI. Components are part of the IPMI. IPMI is a standard and tool set normally available on servers and workstations in business networks. IPMI enables system administrators to handle systems at a reduced, operating system-independent level from distant places. IPMI instruments enable a remote administrator to connect or send PC / server directions and conduct multiple activities, including modifying OS environments, reinstalling OS or upgrading drivers. Baseboard management controllers are at the heart of all IPMI remote management alternatives. BMCs are motherboard microcontrollers, with their own CPU, storage and LAN interface, and act as interface between server / workstation devices and remote sysadmin. They are the element that translates all IPMI commands into local hardware instructions and therefore have complete control over a computer. Due to their access to a BMC interface, they are very limited and secured by a password, generally known only to a company’s sysadmin.
What are the vulnerabilities of USBAnywhere?
However, Eclypsium’s safety scientists today reported vulnerabilities in Supermicro’s BMC firmware in current studies. This vulnerability that you have named USBAnywhere affects the virtual usb function of your firmware which allows sysadmins to connect USB to your own desktop, but it is considered to be a virtual usb linked to a remotely managed system, which transfers information from your local usb to virtual remote. This feature, which is part of the larger virtual BMC Media Service, is a small java application that serves Supermicro-based systems via the standard BMC web interface. Eclypsium researchers said that the authentication problems for this Java application were four:
Authenticated plaintext— While the Java application has a unique authentication session ID, the service also enables the customer to use the username and password in plaintext. Network traffic unencrypted–Encryption is accessible but must be requested from the customer. For the initial authentication package, the Java application supplied with the systems in question use this encryption but then use unencoded packages for all other traffic. Weak encryption— Using a fixed key compiled into the BMC firmware, payload is encrypted with RC4 when encryption is used. All Supermicro BMCs share this key. RC4 has several published cryptographic weaknesses and TLS (RFC7465) is forbidden to be used. Authentication Bypass (only Supermicro X10 and X11 platforms)— Some inner state on that customer is wrongly authenticated by the customer and then disconnected. As the internal status is linked to the client’s socket file descriptor number, this internal state is assigned to the new client, who receives the same socket file descriptor number from the BMC OS.
In practice, this enables the new customer to receive authorisation from the prior customer even if the new customer tries to authenticate with inaccurate credentials.
Patches have been published by Supermicro
Supermicro has recorded all four problems, and the seller has published patches for the Supermicro X9, X10 and X11 boards on its website. “We would like to thank the scientists who found BMC Virtual Media vulnerability,” ZDNet announced last week in an email. The seller also told Eclypsium to work carefully to verify that the fixes worked as planned and should now be used safely. Rick Altherr, Principal Engineer at Eclypsion, informed ZDNet about Supermicro’s fixes, “Core modifications included wrapping the TLS virtual media service, removing plaintext authentication features and fixing the bug leading to authentication bypass.”
The most risky bug
The fourth of the four bugs is the one most probable to cause issues. The bug enables a malicious hacker to start repeated links to the Virtual Media Service of the BMC internet interface (Java app) until they land with a lawful admin on the same server socket. Altherr does not suggest that businesses take a opportunity, although exploiting this vulnerability appears to be an affair of blind luck. “Although the precise circumstances that result in Linux reuse of the socket amount can be complicated and thus mainly blind luck, the VMS one-user model tends to boost opportunities considerably,” said ZDNet. “In our testing, we were able to reliably exploit the BMC authentication bypass for weeks after the legitimate user had used the virtual media service.” In this case, although the attacker has no proper BMC credentials it can interact on the BMC. While imitating an USB looks harmless, the study team from Eclypsium has indicated that the assailant can “boot from malicious USB images, exfiltrate information over the usb mass storage devices or use a virtual usb sticker, Rubber Ducky, which quickly conducts a thoroughly designed series of keystrokes to hack nearly any other form of BMC, firmware or server it operates.”
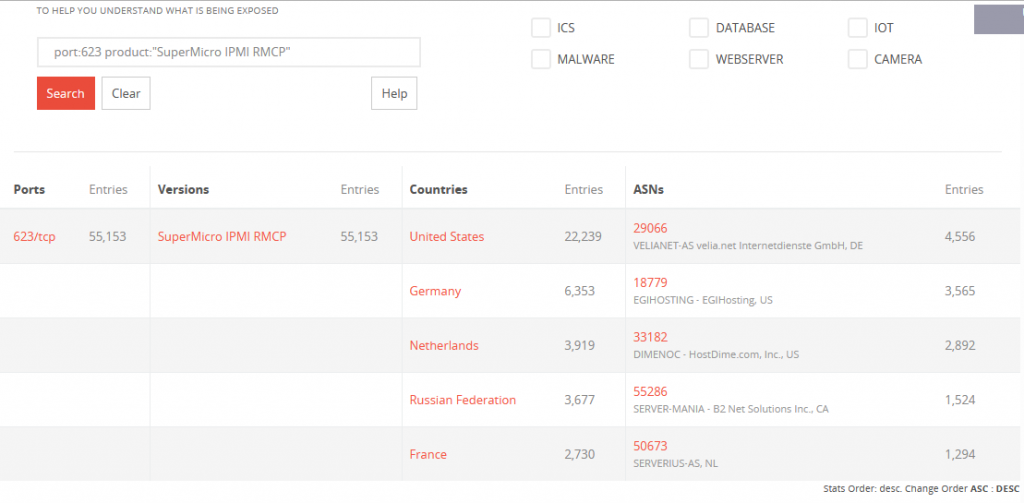
Between 47,000 and 55,000 Supermicro BMCs exposed online
These attacks are dangerous if physically conducted, but they are even more dangerous if they are done through a remote vector such as the Internet. “TCP port 623 scanned across the Internet revealed 47,339 BMCs from more than 90 distinct nations with publicly available virtual media services,” said Eclypsium Researchers. These systems are now at risk of being attacked and possibly damaged. Attackers can use malware on systems that can reinstall OS or even momentarily brick servers to sabotage rivals or extort payments from companies runnering virtual media port BMC exposed systems. A BinaryEdge search prior to publishing this article discovered even more exposed devices— with over 55.000 Supermicro IPMI interfaces that display internet port 623. The vast majority of these devices used the data center and internet hosting networks and exposed them and their corresponding clients to assaults from USBAnywhere.
Supermicro: Set patches up, remove BMCs from the web
“Best practice in industry is to operate BMCs on a remote private network not exposed to the Internet, thereby reducing, but not eliminating, recognized exposures,” a Supermicro spokesman informed ZDNet last week. Customers are advised to install the recent patches to fully mitigate the USBAnywhere attack vector. This is not the first time that safety specialists warn against the Internet access to BMC / IPMI management interfaces. In 2013, 100,000 IPMI-enabled systems of three main Internet providers were discovered by scholars. BMC firmware protection was not a standard at the moment, and all those servers were at risk of malicious variants replenishing their firmware.