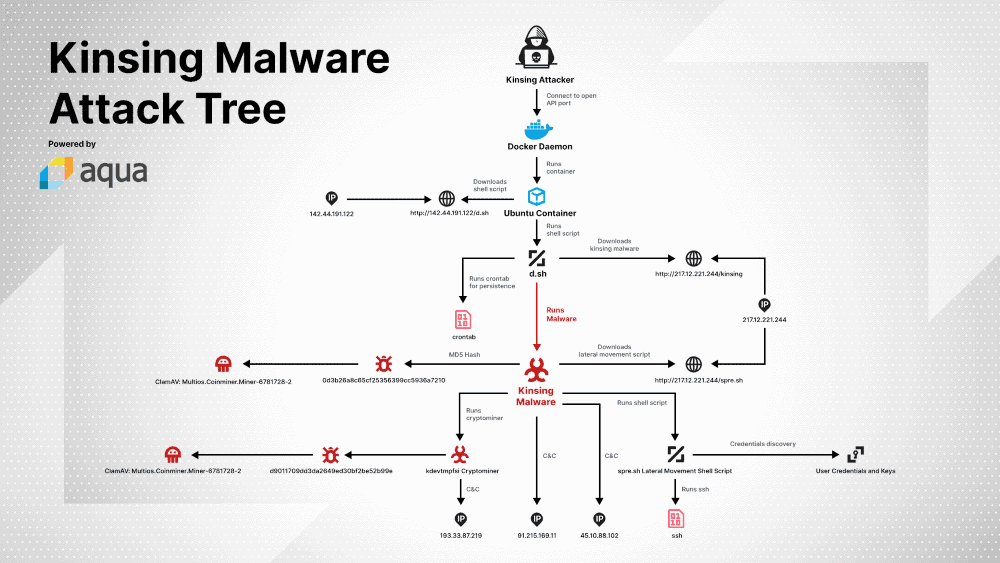
For the last few months, malware operations have searched the Docker server internet for API ports that are exposed without a password on the website. Then hackers break into insecure hosts and mount a new crypto-mining malware strain called Kinsing. According to Aqua Security, the cloud protection firm, which described the campaign in a blog post on Friday, attacks started last year and continue. These attacks are only the last in a lengthy series of malware campaigns that have targeted Docker instances — systems with unrestricted access to vast computer resources when breached. Gal Singer, an Aqua security researcher, reports that hackers use the access given by this port to spin an Ubuntu container when they see a Docker instance with an exposed API port where they download and install the Kinsing malware. The primary purpose of the malware is to mine the cryptocurrency of the hacked Docker case, but there are also secondary functions. Those involve running scripts that delete certain malware that can run locally but gather local SSH credentials to try and spread to a container network in your organization and exploit the same malware on other cloud systems. As malware attacks are still ongoing, Aqua advises that businesses check their Docker instance safety settings to ensure that no official APIs are exposed online. These admin endpoints should either be disabled or deactivated behind a firewall or VPN gateway if they need to be online exposed. The recently released Kinsing malware camp is just the latest in a long line of crypto-mining attacks on Docker services. Such attacks start in spring 2018 for the first time. The first companies at the time to detect attacks on Docker systems were Aqua and Sysdig. Before that, other attacks and malware followed. The Trend Micro reports (October 2018), Juniper Networks (November 2018) and Imperva reports (March 2019), Trend Micro and Alibaba Cloud (May 2019), Trend Micro again (June 2019), and Palo Alto Networks (October 2019) have provided details of other offenses against the Docker servers.