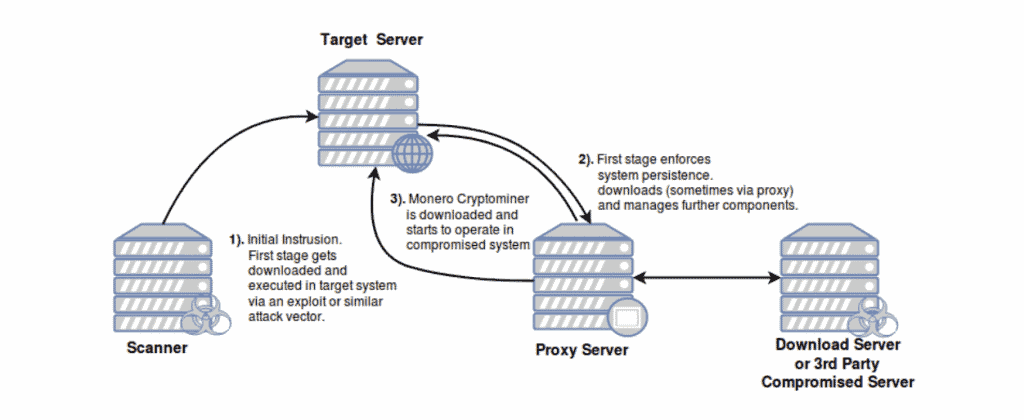
Discovered by Intezer’s security researchers, this new group— which they called Pacha Group — have not directly targeted Linux servers, but the top-run apps. Experts say that Pacha Group hackers use brute-force attacks to compromise services such as WordPress or PhpMyAdmin, and once they have an initial foothold, they increase their access to the underlying server where they deploy their malware in Linux. GreedyAntd (hereafter Antd) by Intezer. In mid-September 2018, a report by a Chinese security researcher places Antd’s first sighting. Intezer says the source code of the malware overlaps with the source code of another strain of malware discovered this year in January and named Linux. HelloBot, also used by the Pacha Group.
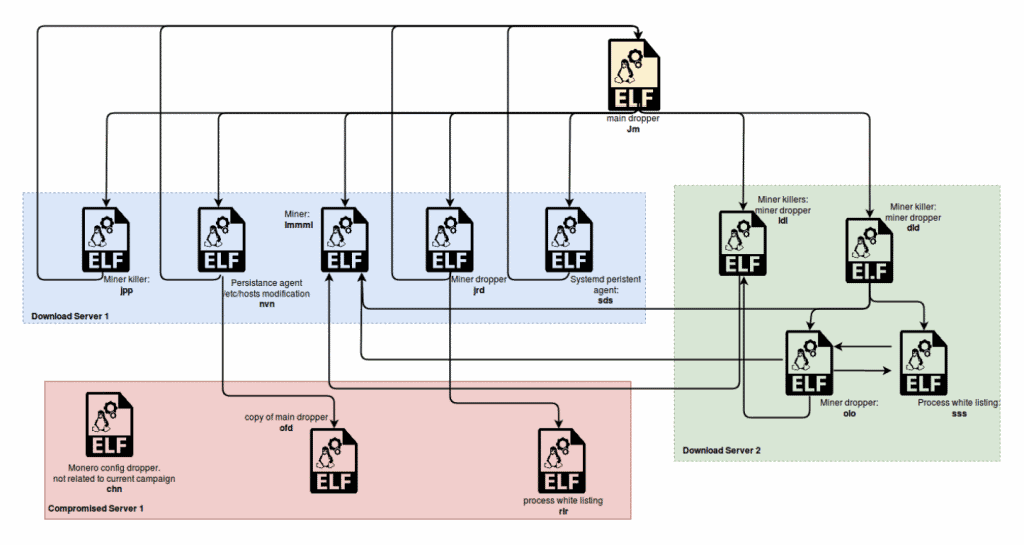
Image: Intezer Signs indicate that hackers develop and test the malware in parallel and then stick to Antd for current operations. Antd is a complex piece of code, designed around a modular structure and designed to work with multiple command and control servers, according to the technical deep dive of Intezer into the inner workings of the malware.
Image: Intezer We can assume that the main reason for having such a broad infrastructure involving a large number of components is to make it more resilient to server shutdowns and to provide a modularity factor, “said the Intezer team.” In addition, having this number of components interconnected with each other also means investing much more effort to clean up a compromised system in question.