Malware Explained: You know how every year the medical community campaigns to get a grip on everyone? This is because flu outbreaks usually have a season — a time of year when people begin to spread and infect. In contrast, seasonal infections for PCs, smartphones, tablets and business networks are not predictable. It’s always a flu season for them. But instead of suffering from chills and body aches, users may become ill with some kind of machine disease — malware. Table of content Malware infections come to us like a torrent of water from a fire hose, each with its own attack methods, from stealthy and sneaky to subtle. If knowledge is power, however, as a preventive inoculation against infection, we offer a short course on malware, what it is, its symptoms, how to deal with it, and how to prevent it in the future.
What is Malware?
Malware is a term used to describe any malicious program or code that is harmful to systems. Malware is hostile, intrusive and deliberately nasty to invade damage or disable computers, computer systems, networks, tablets and mobile devices, often by partially controlling the operation of a device. Like human flu, normal functioning is interfered with. Malware is about illegally making money from you. Although malware cannot damage the physical hardware of systems or network equipment (with one known exception –see the Google Android section below), it can steal, encrypt or delete your computer data, alter or hijack core functions and spy on your computer activity without your knowledge or permission.
How can I tell if I have an infection with malware?
Malware has many different aberrant behaviors to reveal itself. Here are some signs you’ve got malware on your system: Your computer is slowing down. One of the main effects of malware is to reduce the speed of your operating system, whether you browse the Internet or simply use your local applications. A tidal wave of irritating ads that should not be on your screen is washing. Unexpected pop – ups are typical signs of an infection with malware. They are particularly associated with a malware form known as adware. In addition, pop-ups are usually packed with other hidden threats to malware. So if you see something like ” CONGRATULATIONS, you don’t click on it! ” in a pop – up. Whatever the free prize promises, it’s going to cost you a lot. Your system crashes, freezes or displays a BSOD (Blue Death Screen) repeatedly on Windows systems after a fatal error occurs. You notice a mysterious loss of disk space, probably because of a bloated squatter of malware hiding in your hard drive. There is a strange increase in the Internet activity of your system. The use of your system resources is abnormally high and the fan of your computer starts to whirl at full speed — signs of malware activity in the background using system resources. The homepage of your browser changes without your permission. Likewise, links you click to an undesirable web destination. This usually means that you clicked on the pop – up “compliments “that downloaded some unwanted software. Your browser might also slow to a crawl. New toolbars, extensions or plugins will fill your browser unexpectedly. Your antivirus product stops working and you can’t update it, leaving you unprotected from the disabled malware. Then there is a painfully obvious, deliberately unsanitary malware attack. This is famous for ransomware, which advertises itself, tells you that it has your data and requires a ransom to return your files. Even if it seems everything works fine on your system, don’t get complacent, because no news is not necessarily good. Powerful malware can hide deep in your computer without lifting any red flags, stealing sensitive files or using your PC to spread to other computers.
How can I get infected with malware?
The malware infection recipe requires a long list of ingredients. Most commonly, malware accesses your system — the Internet and e – mail. So you’re connected online at all times. Malware can penetrate your computer when (deep breath now) you surf through hacked websites, click on game demonstrations, download infected music files, install new toolbars from an unfamiliar provider, set up dicey source software, open a malicious email attachment, or almost everything else you download from the web to a device that lacks a quality anti – malware security application. Malicious applications can hide in apparently legitimate applications, especially when downloaded from websites or messages instead of a secure app store. When installing applications, it is important to look at the warning messages, especially if you are seeking permission to access your email or other personal data. In short, it’s best to stick to trusted mobile app sources, install reputable third – party apps only, and always download those apps directly from the vendor— and never from any other site. All in all, there is a world of bad actors with an offer for an Internet accelerator, a new download manager, a hard drive cleaner or an alternative web search service. Without the most important ingredient, Malware attacks would not work: That is, a glorious version of you that wants to open an email attachment that you don’t recognize or click and install something from an untrusted source. And don’t take this as “click-shamed, “because even very experienced people have been tricked into malware installation. Even if you install something from a credible source, you might install software that you don’t want if you don’t pay attention to the permission request to install other bundled software at the same time. This additional software is often presented as an essential component, but it is not often. Another wrinkle is a bit of social engineering observed in the UK. The scam hit mobile users by using a common mobile payment option for direct payments. Users visited mobile sites, unwittingly tripping invisible buttons that charge them via their mobile numbers, billing the victims ‘ networks directly and passing the costs on their bills. To be fair, we also need a blameless scenario for malware infection. Because it can even lead to a drive-by malware download by visiting a malicious website and viewing an infected page and/or banner ad. On the other hand, if you do not run an adequate security program, you still have the malware infection and its aftermath.
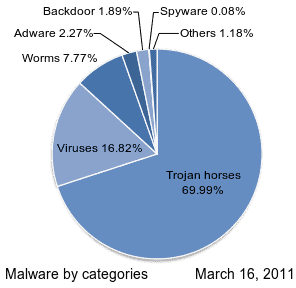
What are the most common malware forms?
Here are the most common offenders in the malware gallery of rogues:
- Adware is unwanted software designed to display advertisements on your screen, usually in a web browser. It usually uses an underhand method to disguise itself as legitimate or piggyback on another program to make you install it on your PC, tablet or mobile device.
- Spyware is malware that secretly observes the activities of the computer user without permission and reports it to the author of the software.
- A virus is malware that attaches to another program and replicates itself when it is executed — usually inadvertently by the user— by modifying and infecting other computer programs with its own code bits.
- Worms are a virus-like malware type that replicates itself to spread over a network to other computers, usually causing harm by destroying data and files.
- The Trojan horse is one of the most dangerous types of malware. It usually amounts to something useful to trick you. The attackers behind the Trojan gain unauthorized access to the affected computer once it is on your system. Trojans can then be used to steal financial information or to introduce threats such as viruses and ransomware.
- Ransomware is a malware form that locks you out of your device and/or encrypts your files and then forces you to pay a ransom for it. Ransomware was referred to as the cybercriminal weapon of choice because it requires a fast, profitable payment in a hard to trace cryptocurrency. The code behind ransomware is easy to obtain through online criminal markets and it is very difficult to defend against it.
- Rootkit is a malware form which gives the attacker the privileges of the infected system administrator. It is also typically designed to keep the user, other system software and the operating system itself hidden.
- A keylogger is malware that records all keystrokes of the user on the keyboard, typically stores the information collected and sends it to the attacker who is looking for sensitive information such as usernames, passwords or credit card information.
- Malicious cryptomining, also sometimes referred to as drive-by mining or crypto jacking, is a malware that is usually installed by a Trojan. It allows someone else to mine crypto currency, such as Bitcoin or Monero, using your computer. Instead of allowing you to cash in on the horsepower of your own computer, the cryptomers send the collected coins to their own account and not to yours. In essence, a malicious cryptominer is stolen to make money.
- Exploits are a malware type that uses bugs and vulnerabilities in a system to control the exploit creator. Among other threats, exploits are linked to malware, which attacks via a legitimate site that unwittingly extracts malicious content from a bad site. The bad content then tries to install itself in a drive-by-download on your computer. No click is required. You just have to visit a good website on the wrong day.
History of Malware
Given the variety of malware types and the large number of variants released in the wild daily, a complete malware history would be a list that would be too long to include here. That said, the trends in malware in recent decades are easier to manage. Here are the main developments in malware.
1980s and later: the theoretical basis of ” automatic self-reproduction ” (i.e., viruses) dates back to an article published in 1949 and early viruses occurred on computer platforms in the 1970s. However, the history of modern viruses starts with the Elk Cloner programmer, which started to infect Apple II systems in 1982. Disseminated through infected disks, the virus itself was harmless, but spreads to all disks attached to a system and explodes so virulently that it can be considered the first major computer virus outbreak in history.Please note this was before any Windows PC malware. Viruses and worms have since become widespread. The 1990s: This decade, the Microsoft Windows platform and the flexible macros of its applications led malware authors to write infectious code in Microsoft Word and other programs ‘ macro languages. These macro viruses infected documents and templates instead of executable applications, although the Word document macros are strictly speaking an executable code form. 2002 to 2007: Instant messaging worms — self – replicating malicious code spread over an instant messaging network — take advantage of massive network loopholes, infecting the AOL AIM network, MSN Messenger, Yahoo Messenger, and corporate instant messaging systems. 2005 to 2009: Adware attacks proliferated and unwanted advertisements were presented to computer screens, sometimes in the form of a pop – up or a window that users could not close. These ads often used legitimate software as a means of spreading, but software publishers started suing adware companies for fraud in around 2008. The result was money worth millions of dollars. This eventually shut down adware companies. 2007 to 2009: Malware scammers turned to social networks like MySpace as a rogue advertising channel, redirects and offers fake antivirus and security tools. Their ploys have been designed to fool consumers through tricks in social engineering. After MySpace became less popular, Facebook and Twitter became the most popular platform. Common tactics included fake links to phishing pages and the promotion of malicious extensions to Facebook applications. When this trend diminished, scammers explored other ways of stealing. 2013: a new malware form called ransomware launched a CrytptoLocker attack, which continued from early September 2013 to late May 2014, targeting Windows – based computers. By the last quarter of 2013, CryptoLocker succeeded in forcing victims to pay about $ 27 million. In addition, the success of the ransomware spawned other similarly named ransomware. Between April 2014 and June 2015, one copycat variant netted more than $ 18 million of some 1,000 victims. 2013 to 2017: delivered through Trojans, exploits and malware, ransomware became the king of malware, culminating in enormous outbreaks in 2017 affecting all kinds of businesses. Ransomware works by encrypting the data of the victim and then asking for payments to be released. 2017 to present: Cyptocurrency — and how to mine for it — has received widespread attention, leading to a new malware scam called crypto jacking, or a secret use of someone else’s device to surreptitiously mine crypto currency with the resources of the victims.
Does Macs receive malware?
Conventional wisdom has sometimes shown that Macs and iPads are immune to (and do not need an antivirus) capture of viruses. That’s true for the most part. At least, in a long time it didn’t happen. Mac systems are vulnerable (and subsequent infection symptoms) to Windows machines and cannot be regarded as bulletproof. For example, the integrated malware protection of the Mac does not block all adware and spyware packaged with fraudulent downloads of applications. Other threats are Trojans and keyloggers. The first detection of ransomware specifically written for the Mac occurred in March 2016 when more than 7,000 Mac users were affected by a Trojan attack. Actually, in 2017, malware on Mac is found. Number of new unique threats on the Mac platform was more than 270 percent higher than in 2016.
Does mobile device get malware?
Criminals of malware love the mobile market. After all, smartphones are complex and sophisticated manual computers. They also offer an entry into a treasure trove of personal information, financial information and all kinds of valuable data for those who want to make a dollar dishonest. This has unfortunately led to an exponentially growing number of malicious attempts to exploit smartphone vulnerabilities. Malware can be found on your phone in a number of ways from adware, Trojans, spyware, worms and ransomware. Some obvious culprits are clicking on a dodgy link or downloading an unreliable app, but you can also get infected by emails, texts and even your Bluetooth connection. In addition, malware like worms can spread from infected phones to other phones. The fact is, the market is enormous (read: target). One statistical source puts the number of mobile device users worldwide at 2.1 billion, with a projected increase to 2.5 billion by 2019. A quarter of these users have more than one apparatus. Fraudsters find the mobile market extremely attractive and use a huge economy of scale to leverage their efforts. Often mobile users are easier to target too. Most do not protect their phones as diligently as their computers, do not install security software or update their operating systems. They are therefore vulnerable to primitive malware. Since the screens of mobile devices are small and users cannot easily see activity, typical red – flag behaviors that signal an infection in a PC, like spyware, can run behind the scenes in stealth mode. Mobile devices infected pose a particularly insidious risk in comparison to a PC. You can follow every move and conversation with a hacked microphone and camera. Even worse, malware for mobile banking intercepts incoming calls and text messages to avoid the two – step security of authentication that many banking apps use Keep in mind that cheap phones can be pre – installed with malware that can be cleaned almost impossible. Google’s Android and Apple’s iOS are the two most common smartphone operating systems in the mobile malware ecosystem. Android has 80% of all smartphone sales on the market, followed by iOS with 15% of all smartphones sold. No big surprise then that the Android platform is more popular than the iPhone. Let’s look at each of them separately.
How do I tell my Android device whether it has malware?
Fortunately, if your Android phone gets infected, there are some unmistakable red flags that wave you. You may become infected when you see one of the following:
How do I tell if I have malware on my iPhone or iPad?
If the name of your smartphone starts with a lower case “i,” part on the back because malware is not a major problem on the iPhone. This doesn’t mean that it doesn’t exist, but it’s very rare. Actually, a malware infection on an iPhone usually occurs only in two exceptional circumstances. The first is a targeted attack by a nation – state adversary— a government that has either created or purchased a piece of malware designed to take advantage of some obscure security hole in the iOS at a cost of millions of dollars. Do not be shocked, as all devices are vulnerable. Apple has certainly done a fine job of securing iOS, preventing applications (including security software) from scanning the phone or other apps on the device’s system. This is why it is so expensive for malware engineers that they install their code for any remotely carried out activity that offends national needs. One particularly notable example occurred in 2016 when an internationally recognized human rights defender based in the United Arab Emirates (UAE) received text messages on his iPhone promising ” new secrets ” about tortured prisoners in UAE prisons. The target recipient was encouraged to click on the link included. He did not send the message to cybersecurity researchers, who identified it as a feat that would have turned the activist’s phone into a digital spy. The second example is when a user makes an iPhone vulnerable by removing the restrictions and limitations imposed by Apple, mainly to ensure that software apps can only be installed from the App Store. Apple carries the app developers carefully, even if malware piggybacking has happened on a legitimate app. Another point, although straightforward malware infections are unlikely, an iPhone does not protect you from scam phone calls or text messages. If you tap a link in a message from an unknown source (or someone you know is impersonated or “spoofed “), you can be sent to a site that requests your login and other personal data. There are many ways you can still become a victim. Always proceed cautiously.
Who are targets of malware?
Millions of consumer devices are out there. They are linked to banks, shop accounts and anything else that is worth stealing. It is a wide attack surface for adware and spyware, keyloggers and malware— and an attractive method for lazy criminals to create and distribute malware to as many targets as possible, with little effort. Cyptominers and suppliers of ransomware seem to have equal opportunities with regard to their objectives. Individuals, like corporate companies, hospitals, municipalities and retail stores, are the victims of these two. It is not only consumers who target mobile spyware criminals. If you use your smartphone or tablet at work, hackers can turn their attacks on your employers via mobile device vulnerabilities. In addition, the incident response team of your company may not detect breaches caused by the use of corporate email by a mobile device. Again, not all apps available through Apple’s App Store and Google Play are desirable and the problem with third – party app stores is even more acute. While the app store operators are trying to prevent malicious apps from penetrating their website, some inevitably pass. These applications can steal user information, try to extort money from users, try to access corporate networks to which the device is connected, and force users to view unwanted ads or engage in other unhealthy activities.
How can I get rid of malware?
If you suspect malware — or you just want to be careful— you should take a couple of steps. First, if you don’t already have one, you can download a legitimate anti – malware program. Then install it and perform a scan. Such programs are designed to search for and remove any malware on your device. Once the device is clean, it is a good idea to change your passwords, not only for your PC or mobile device, but also for your e – mail address, social media accounts, favorite shopping sites and online banking and billing centers. If your iPhone gets infected with something nasty somehow, things are a bit more difficult. Apple does not allow scanning the system of the iPhone or other files. Your only option is to wipe your phone with a factory reset and restore it from your backup.
How can I protect myself against malware?
Stay alert. Pay particular attention if you see a domain name ending in a strange set of letters, i.e. something other than com, org, edu or biz, to name a few, as they can be a risky website indicator. “Ensure that your operating system, browsers and plugins are always up – to – date.” Pay close attention to early signs of malware infection for all your devices to prevent them from burrowing. When browsing the internet, avoid clicking on pop – up ads. Remember to open unsolicited email attachments or download software from untrusted websites or peer – to – peer networks. Make sure your operating system, browsers and plugins are always up – to – date, as you can keep your software patched online. Only download apps from the Google Play Store for mobile users (the app store is the only choice for iPhone). Whenever you download an app, first check your ratings and reviews. If the rating is low and the downloads are low, it is best to avoid this app. Do not download apps from sources from third parties. Go to your Android device’s Settings and open the security section. Make sure that Unknown Sources is disabled so that apps from markets other than the Play Store are not installed. Do not click on strange, unchecked links in unknown emails, texts and WhatsApp messages. Odd links between friends and contacts should also be avoided unless you have verified that they are safe. In order to keep their businesses safe, companies can prevent malicious apps from threatening their networks by creating strong mobile security policies and implementing a mobile security solution that can enforce them. This is essential in today’s business environment— with multiple operating systems operating under multiple roofs. Finally, get a good anti – malware program for yourself. It should include layered protection (the ability to scan and detect malware like adware and spyware while maintaining a proactive real – time defense capable of blocking such threats as ransomware). Your security program should also remedy any system changes from the malware it cleans, so that everything returns to normal.