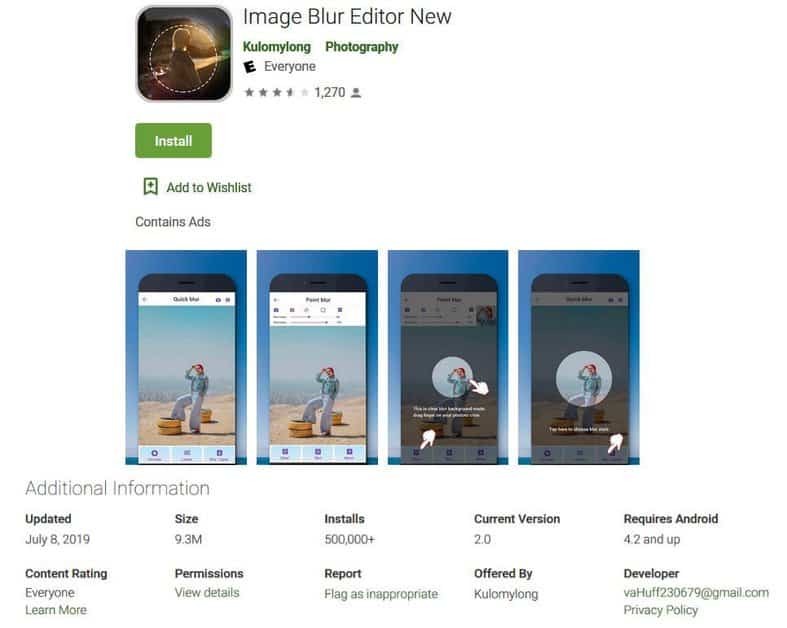
The 25 applications were discovered in the Play Store in late August and while they did not display malice instantly after installation, the applications then download malware settings documents to turn on “evil” mode. These will inform the bundled malware parts to allow modules that are intended to conceal the icons of applications and to begin displaying advertisements that allow malware developers to make cash from Android infected devices. Malicious app with 500,000 installs
Google Play Protect bypassed
After all 25 apps were effectively discovered by Google on September 2nd, all camouflaged as fashion and picture utilities were deleted by checking that the malicious features were not hardcoded for check-in in the APKs (Android Package Kits). “The switch is instead remotely controlled via the downloaded configuration file so that the malware developer avoids the strict safety testing Google Play has done,” tells Symantec’s Threat Intelligence team, which has found the applications. “These 25 malicious and hidden applications share the same code structure and application material, leading us to think that developors could either be part of the same organizing community or use at least the same source code base.” Threats performers used initializing vectors and crypting keys to encode and encrypt keywords in the malware to prevent having their applications recognized as malicious.
Malware configuration files
Random advertisements shown, top graphs abused
The applications are intended to conceal from view first by removing your icons and then begin displaying advertisements on the affected systems even when the applications are closed. “Full-screen ads are displayed in the advertisement window at random intervals, so consumers have no way of understanding which app is accountable for conduct,” claims Symantec’s report.
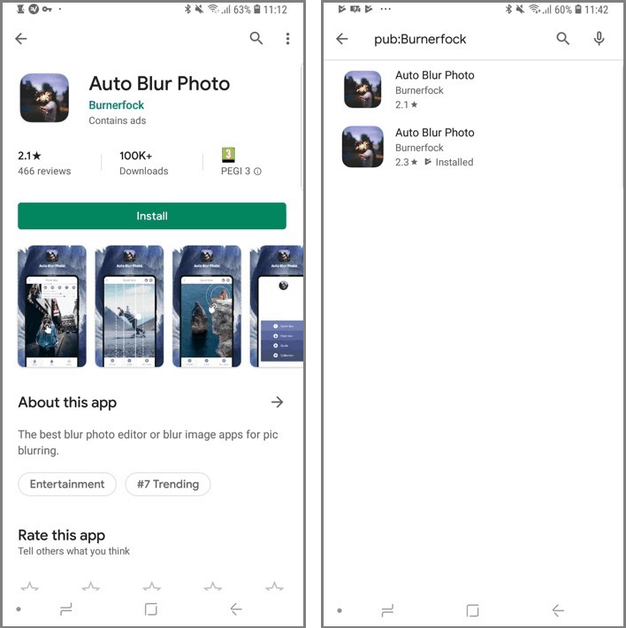
Malware configuration files One of the designers behind the applications used an innovative manner to get a malicious app to their objectives: two identic applications, one clean and one with bundled malicious code, were released in the shop. The clean one was promoted to the Top Trending Apps category of the Play Store in the hope of accidentally installing the malicious copy and infecting users with the aggressive malware ad-pushing.
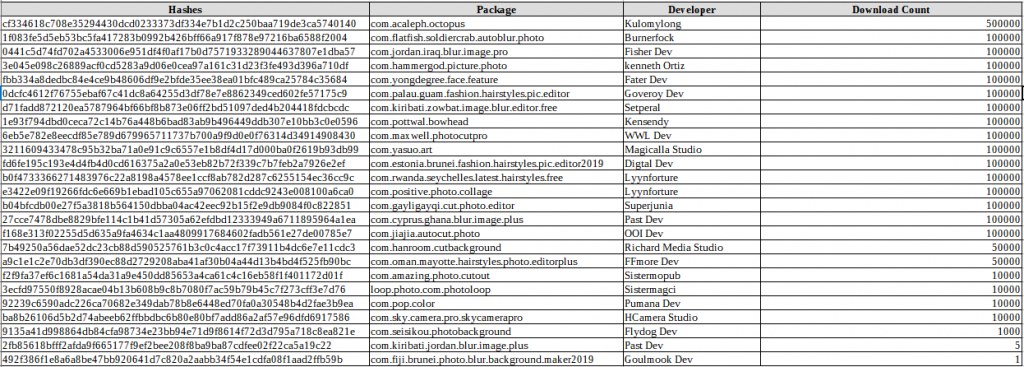
Indicators of compromise (app IDs, hashes, download counts) At the end of the Symantec Threat Intelligence team’s analysis, you can obtain a full list of compromise indicators (IOCs), including application ids (package names), hazards, developer names, and download counts for each of the 25 malicious applications.