The accompanying Unix crypt(3) hash sorts of the create tools John the Ripper: traditional DES, “big-crypt,” BSDI-based extended DES, FreeBSD MD5 (additionally used on Linux and Cisco IOS) and OpenBSD-based Blowfish (which has also been used on some Linux dispersions and enhanced by late Solaris). In addition, Kerberos / AFS and Windows LM (DES-based) hashes and DES-based tripcodes are also supported out of the case. John the Ripper is available on various platforms, allowing you to use a similar cracker everywhere. John’s Ripper Pro includes support for both the salted hashes Windows NTLM (MD4) and Mac OS X 10.4+.
Linux Hashes Extraction
Each Linux user knows that the hashed passwords are stored in /etc / passwd, you can see this folder using the root@kali command ~ # cat / etc / passwd We can see the code compromised like X, so we should unmask the password by unmasking the key. Now use the unshadow command to unmask / decrypt passwords. root@kali:~# unshadow /etc/passwd /etc/shadow > hashfile /etc/passwd : Password location /etc/shadow : Shadow file hashfile : Output file You can now see that the real hash values have replaced the X. For John the Ripper we can use different cracking modes, we must use simple and powerful wordlist mode. root@kali:~# john –wordlist=/usr/share/john/password.lst hashfile The cracked passwords can be accessed by the command in john.pot root@kali:~# cat /root/.john/john.pot On the screen, we can see the password: test123.
Extracting Windows machine hash dumps
Pwdump is an important simple, handy tool for the LM and NTLM secret word hackers of the Security Account Manager (SAM) local client accounts. In the working directory, download and extract pwdump. Just typing pwdump into the command prompt allows us to get the local client account hashes from the SAM database. We can also extract the hashes into the file pwdump7 > hash.txt
Cracking with John the Ripper
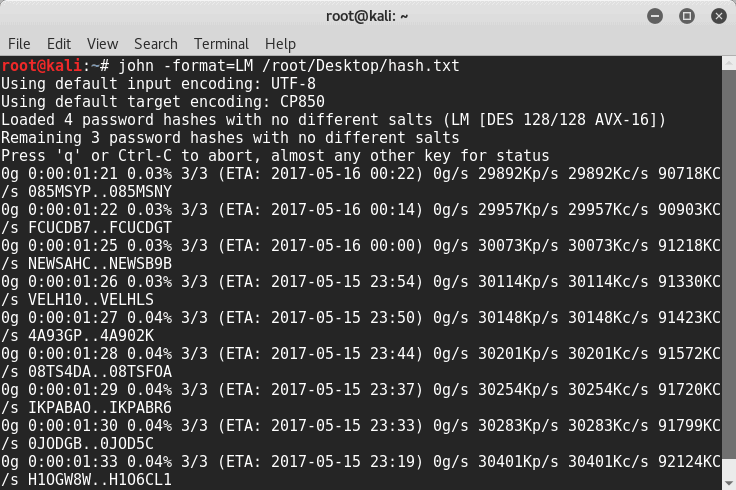
John the Ripper’s offline password is meant to be rich and fast. By typing, you can get all possible options root@kali:~# john -hTo list all the possible formats root@kali:~# john –list=formats To list all the possible subformats root@kali:~# john –list=subformats To bruteforce the root@kali:~# john -format=LM /root/Desktop/hash.txt
It will take a while to crack the code. Ultimately, John the ripper is a great tool for cracking offline passwords. Don’t use it for purposes of offense.