Crooks use phishing to trick prospective victims into transmitting sensitive data through fraudulent websites, which they use a broad variety of social engineering methods as well as message that seems to have been sent by someone they know or by a lawful organisation. In this event, the phishing messages sent by the attackers behind this campaign use fake Instagram login alerts to indicate that somebody has tried to log in to the target account, requesting that the attacker confirm the identity through a sign-in page connected to the email.
Authentication codes for adding legitimacy
These messages are intended to look as closely as possible as to formal texts from Instagram to prevent any suspicions before the goal is redirected to the phishing section of the attackers. “Apart from a few punctuation errors and the missing space before the word ‘Please’, this message is clean, clear and low-key enough not to raise instant alarm bells,” details Sophos’ Paul Ducklin who analyzed the campaign. The crooks add a code that should apparently be used as a second ID authentication code to further improve the illusion that they are official Instagram alerts. “The use of what looks like a 2FA code is a neat touch: the implication is that you aren’t going to need to use a password, but instead simply to confirm that the email reached you,” Ducklin adds.
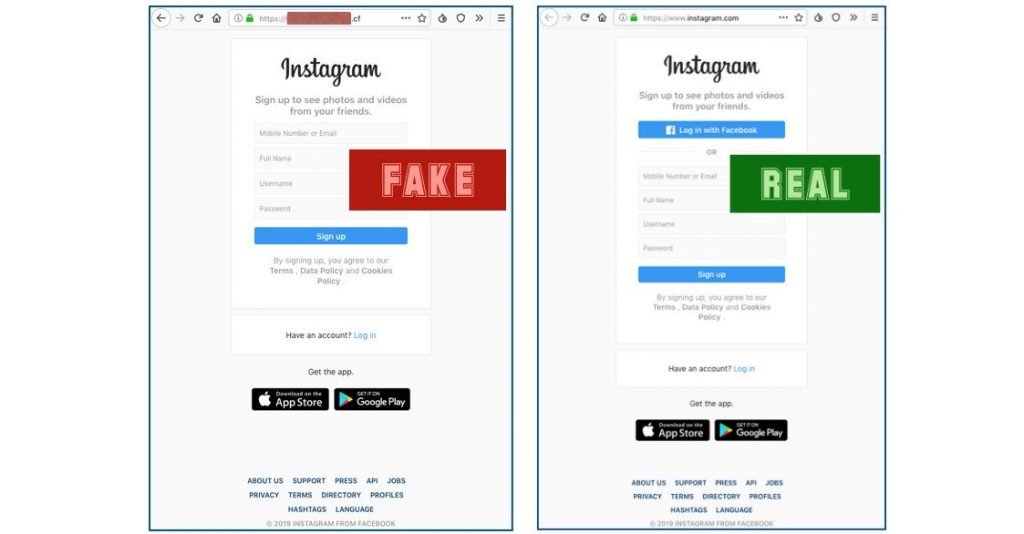
Instagram phishing email sample Once on phishers ‘ landing page, the aims of the Instagram login page will be fully cloned and secured using a valid HTTPS certificate and a green padlock will show all doubts that the agreement is true. Instead of displaying the instagram.com domain in the address bar of the web browser, the phishers use the.CF domain (a state code of the highest level for the Central African Republic). This shows that even though the green clock says the link is protected, it also requires checking whether the domain is a lawful one used by the website or service. “If we had to guess, we’d suggest that the crooks didn’t get quite as believable a name as they wanted because they went for a free domain name,” explains Ducklin.
Phishing page vs Instagram login page
What to do after you have been hacked
This isn’t the first or the last phishing campaign targeting users in Instagram and certain customers are bound to fall for this scam, since the crooks come back with fresh assaults. In April, for example, two distinct series of Instagram phishing attacks called’ The Nasty List’ (The Blasty List) and’ The Hotlist’ were wrapping up the social network and following user login credentials. In the event that your Instagram credentials have been stolen or your account hacked but you still have access to your account, first check that your right e-mail address and phone number still have access to your account. You have to go to your profile and grab Edit Profile and then scroll down to see email address and telephone number. Try to enter your right information if you have been swapped with attacker-controlled ones. After that, you should alter the password of the account by following these Instagram directions. The shift in your password will allow you to automatically log out all your presently logged into your account devices so that you can log back in to regain control of your Instagram account. Below are the guidelines for Instagram if you can still log into your account: • Change your password or send yourself a password reset email • Revoke access to any suspicious third-party apps • Turn on two-factor authentication for additional security However, if you missed access to your account after your Instagram account was hacked, you can use these directions to report the event to the safety of Instagram. After verification of your identity, Instagram will reinstate the photo or “the email address or the telephone number you signed up with and the device type you used when signing up.”