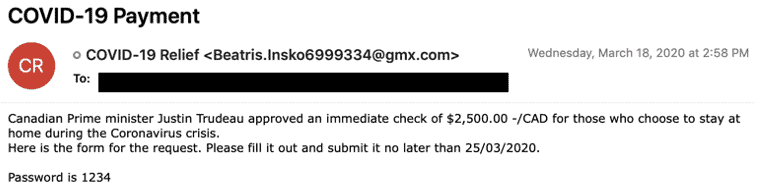
FireEye, which monitors malware as SILENTNIGHT, reported seeing malicious emails in the “individuals in companies across a wide variety of industries and geographies” inboxes. Emails have the subject line “COVID-19 payment” and contain malicious documents called “COVID 19 relief.” Emails seem to target primary users in the US, Canada, and Australia and targets in ea. The emails sent to Canadians state that the payment authorized by Canada’s prime minister, Justin Trudeau, and they assert that if they fill out a questionnaire, the recipient will receive a check for 2,500 Canadian dollars. The sum is 2,500 Australian dollars, in the messages sent to Australians.
Researchers from MalwareHunterTeam said one of the malicious emails sent to someone at the Vancouver Police Department.
— MalwareHunterTeam (@malwrhunterteam) March 19, 2020 The attached Word document is password-protected, but the password is included in the email file. When users open the report, they instructed to allow macros, which lead to a download to their computer of the Zeus Sphinx banking trojan. Zeus Sphinx, who also identified as Zloader and Terdot, first appeared in 2015, when it only targets UK bank customers. It later started targeting banks across North America, Brazil, and Australia. The primary purpose of the malware is to collect online banking credentials and other personal information by showing phishing pages while the user is navigating to the website of a bank. IBM claims the Trojan removed from the threat environment for almost three years, but now it seems to have resurfaced, and the version used in the latest attacks is just marginally different from the original. In addition to this initiative, FireEye has seen the sending of phishing emails entitled “Internal Guidelines for Business Grants and Loans in Response to COVID-19” to the employees of US financial services organizations. The files attached to those emails lead to a fake message from the US Small Business Administration that brings victims to a phishing page designed to harvest credentials from Microsoft account. FireEye claims that the US newly implemented stimulus bill and other financial aid programs that come in response to the coronavirus epidemic could contribute to a spike in these forms of attacks in the coming weeks. The coronavirus pandemic has been used for a wide variety of campaigns by threatening actors, including distributing malware, phishing, and scams, and Proofpoint estimated on Friday that 80 percent of the threats it saw have in some way leveraged the outbreak. US and European authorities recently issued alerts of increased malicious cyber-activity associated with COVID-19.