Threat actors or nations seeking to degrade the efficiency of the Tor anonymity network can do this at inexpensive prices, and fresh academical study has revealed that for only a few thousand US dollars per month. Threat performers can use instruments as banal as government DDoS stresses (booters) to slow down Tor’s downloads and block access to Tor’s censorial capability according to scientists from Georgetown University and the US Naval Research Laboratory. Academics say that whilst an assault on the entire Tor network requires enormous DDoS (512,73 Gbit / s) resources and costs around $7,2 million per month, it provides much easier and more targeted means for all consumers to degrade Tor efficiency. Research submitted at the USENIX safety conference this week showed the feasibility and impacts of three kinds of’ DoS bandwidth assaults’ that can wreak havoc on Tor and their users. Researchers contend that while these attacks are not completely shut down or block the Tor system, they can be used for deterring or driving customers away from Tor because of prolonged bad results, which can be an efficient long-term approach.
I. Targeting Tor bridges
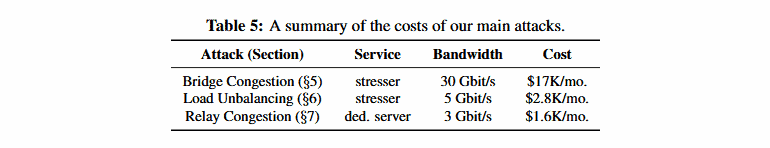
The study team has evaluated in the first DDoS attack scenario that a threat actor can target Tor bridges instead of attacking every Tor server. Tor bridges are special servers that serve as Tor network entry points. However, as opposed to Tor guard servers, their IP-addresses are not listed in public directories, so they cannot be easily blocked. Users living in nations that have blocked access to the Tor Guard server by local government can configure the Tor Browser to use a dozen of built-in bridge servers to overcome any attempt at Tor censorship. But scientists said that all of the Tor bridges are not presently in use and that it costs about $17k / month to saturate traffic to all people (presently 12 operating Tor bridges). Should all 38 Tor bridges be restored and operational, the attack would cost $31k / month, a price tag for any country willing to prevent citizens and dissidents from accessing the Tor network.
II. Targeting TorFlow
A second DDoS attack scenario would be if threatening actors targeted TorFlow, a load balancing scheme of the Tor network, which measures the capability of Tor relays and distributes traffic, thus preventing Tor servers from overpowering themselves and becoming slow. Academics have said it would cost only $2.8k / month to target all TorFlow servers with continuous DDoS assaults using government DDoS booter facilities, even less than they analyzed the first attack. “We discover that such an attack decreases the average customer download rate by 80% by means of high-fidelity network simulation[…],” scientists said.
III.Targeting Tor relays
And for the third type of DDoS attack, scholars have chosen to target Tor relays, the most prevalent type of Tor servers and those that bounce Tor traffic to protect anonymity. Instead, however, the researchers attempted to use DDoS stressors which are mostly used to funnel big amounts of traffic at a destination by exploiting faults in the Tor protocol itself. These service denial errors use logic errors to slow down the Tor protocol, and decrease Tor content download times. For years, such defects have existed and have been effectively used in the past-although these problems have been patched lately by the Tor Project team. During their simulation, however, researchers have shown how much one of these assaults would cost the whole Tor network and not just a Tor-based. According to the study team, an intruder could improve the average Tor download time to just $6.3k / month by 120 per cent and to only $1.6k / month by 47 per cent.
In the budget, of course
Considering that the majority of nation states have millions of dollars in their budgets, these assaults are more than viable. Nation-states are known to sponsor DoS attacks, and the ease of deployment and low cost of our attacks suggest that state actors could reasonably run them to disrupt Tor over both short and long timescales,” researchers said. “We speculate that nation-states may, e.g., choose DoS as an alternative to traffic filtering as Tor continues to improve its ability to circumvent blocking and censorship.”
Moreover, the research team argues that, in comparison to earlier Sybil attacks, the second and third attacks they analyzed also produce better results for cash invested by a threat actor (where a malevolent threat actor introduces rogue servers in the Tor Network to increase traffic imbalance). That is, it’s cheaper and more reliable to decrease the performance of the Tor network than to decrease its traffic. Academics have also proposed some basic mitigations to tackle these threats to the Tor ecosystem. “We recommend additional financing for gentle bridges, moving away from centralized scanning load balancing approaches and improved Tor protocols (in particular the use of authenticated SENDME cells),” they said. The problem with these mitigations is that they are relying on increased funding from the Tor project, a problem that the organization has sought to resolve as Tor is increasingly popular. Details on this research are provided in a white paper called “Point Break: A Study on Bandwidth Denial-of-Service Attacks Against Tor,” presented this week by the Research Team on the 28th USENIX Security Symposium in Santa Clara, USA.