Initially recognized in 2014 by Kaspersky’s Global Research and Analysis Team scientists, the hacking group also known as Inception[ 1, 2] has an history of targeting government agencies and entities from a broad spectrum of sectors through spear-phishing campaigns. Whereas the malware and tactics, techniques and procedures (TTP) used in Cloud Atlas have remained unchanged during its activities since at least 2018, the APT Group has now introduced a malicious HTA malware dropper and VBShower in the form of a polymorphical HTML application.
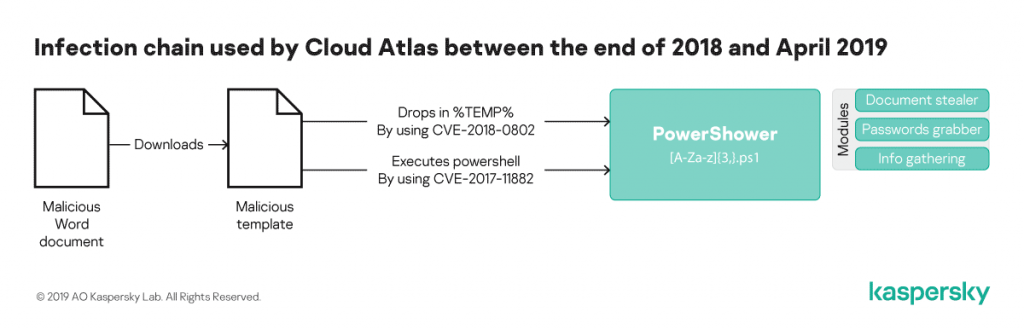
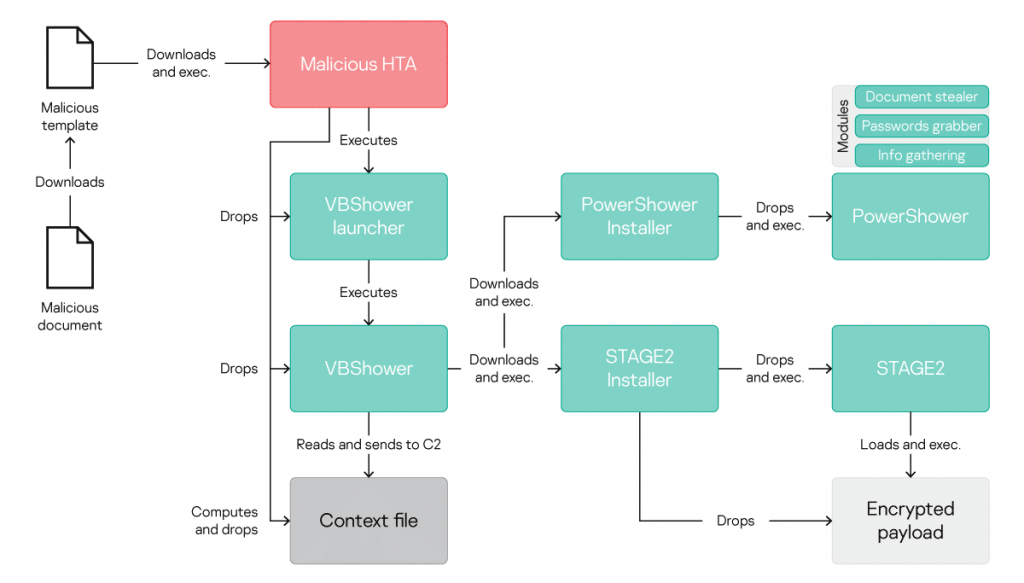
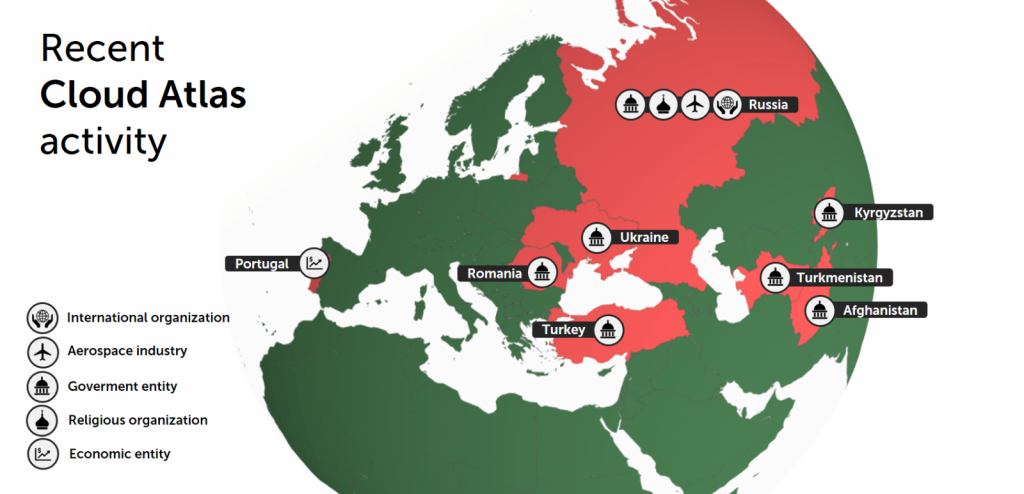
Kaspersky’s study team for compromise devices owned by organisations from Central Asia, Eastern Europe and Russia has noted the new infection chain Cloud Atlas to infect its objectives beginning with April 2019. After effectively infiltrating target systems, performers will use the document stealer of their malware, password collection, and data collection modules to retrieve and exfiltrate data sent to control and control (C2) servers controlled. In contrast to past campaigns by the menace group that began by dropping its PowerShower-based validator implant, after exploitation of the Microsoft Office faults in CVE-2017-11882 and CVE-2018-0802, fresh assaults observed by Kaspersky begin by downloading and launching the polymorphic HTA. “The newly updated chain of infection postpones the execution of PowerShower until a later stage. Instead, after the initial infection, a malicious HTML app is now downloaded and executed on the target machine,” says the report. New Cloud Atlas infection chain “That application will then obtain original computer data, and download and run VBShower, another malicious module.” The PowerShower backdoor which replaces PowerShower as a validator module is then used to download and run a PowerShower installer or other Cloud Atlas 2nd phase backdoor installer that has earlier been identified and evaluated. Right before the second phase of installation, after instructions from the masters, VBShower will also ensure that all proof of a malware is deleted from the compromised systems. “The primary differentiator is that a malicious HTML application and the VBShower module are polymorphic,” the scientists add. “This fresh chain is more complex than the prior model. This means that the hacking group always can infect its objectives using modules which appear to be unique and new, making it much more difficult, if not impossible, to detect their malicious implants with the assistance of earlier discovered IOCs.
IoC has become obsoldered as a reliance instrument to identify a targeted attack in your network, first creating a distinctive set of IoCs for each of its victims and continuing the trend to utilize open source instruments rather than special ones for spy activities,” suggests GReAT reseacher Felix Aime. “Well, this is continuing with this latest instance of polymorphic malware. This does not necessarily imply that actors become increasingly hard to capture, but that safety abilities and the toolkit of the defender have to be evolved along with the toolkit and abilities of the malicious actors they are monitoring.”