The new malicious so-called skip-2.0 tool allows an attacker to connect to any database account using a so-called’ Magic Password,’ while keeping their operation off the security logs. “This loophole allows the attacker to continue with the use of a special password in the MSSQL Server of a victim and to remain undetected by several log and event release mechanisms that are disabled when this key is used,” says ESET researcher Mathieu Tartare.
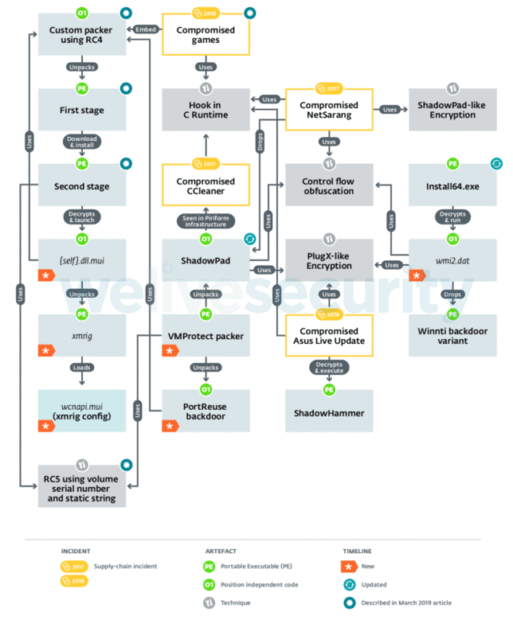
Winnti Group’s arsenal is growing
The Winnti Group is the umbrella term of a Chinese state-supported hacking group (tracked by Symantec as Blackfly and Suckfly, Wicked Panda by CrowdStrike, Microsoft BARIUM, FireEye APT41), which uses the same malicious methods that have been in use since 2011. This is when Kaspersky found the Winnti Trojan hacker on a large number of compromised game systems after it was delivered via the official update server of a game. After an analysis of the new backdoor, researchers from ESET also found that skip-2.0 shares some traits of malware from other Winnti Groups, “particularly PortReuse and ShadowPad backdoors.”
Winnti Group artifacts and TTPs The Winnti hackers used PortReuse, a lightweight Windows backdoor to attack the Asian high profile mobile software and hardware manufacturer’s server. In addition, PortReuse “is a network implant which is already listening to the network and waits for a magical packet to cause malicious code” ShadowPad is another Winnti backdoor used by the group as part of an attack on the 2017 supply chain that affected NetSarang, a soth-korean network connectivity solution provider, when the hacker group succeeded All three backdoors use the same VMProtected launcher and the group custom malware packer and also share several other similarities with several other tools linked to the previous operations of the threat group.
Attacked MSSQL Server 11 and 12
Once the MSSQL database has been deployed, the backdoor skip-2.0 can insert its malicious code through the sqllang.dll method, hooking multiple functions that are used to monitor authentication. This means that the malware could circumvent the built-in authentication mechanism of the server and therefore allow its operators to log in despite the fact that their password does not fit. “This hook feature checks if the user’s password matches the magic password, in which case it does not call the original and the hook returns0, allowing the link even if the appropriate password has not been given,” says ESET. “We triedSkip-2.0 against several versions of MSSQL Server and noticed that we could only successfully login with the Special Password on MSSQL Server 11 and 12,” continues Tartare.
Skip-2.0 injection While MSSQL Server 11 and 12 are not the latest updates, releases in 2012 and 2014 are the most recent, according to ESET researchers from Censys. “The backdoor skip-2.0 is an interesting addition to the arsenal of the Winnti Group, which share many similarities with the already known tool set of the group and allow the attacker to persevere on the MSSQL Server,” concludes the research team at ESET. “Because administrative privileges for installing the hooks are necessary, skip-2.0 on already compromised MSSQL servers must be used to achieve persistence and stealth.”