Avast and Emsisoft, two cyber security companies known for antivirus products, today released free decryptors that can help the victims of ransomware BigBobRoss recover their data without paying ransom demand. Both decrypters can be downloaded from both Avast and Emsisoft sites.
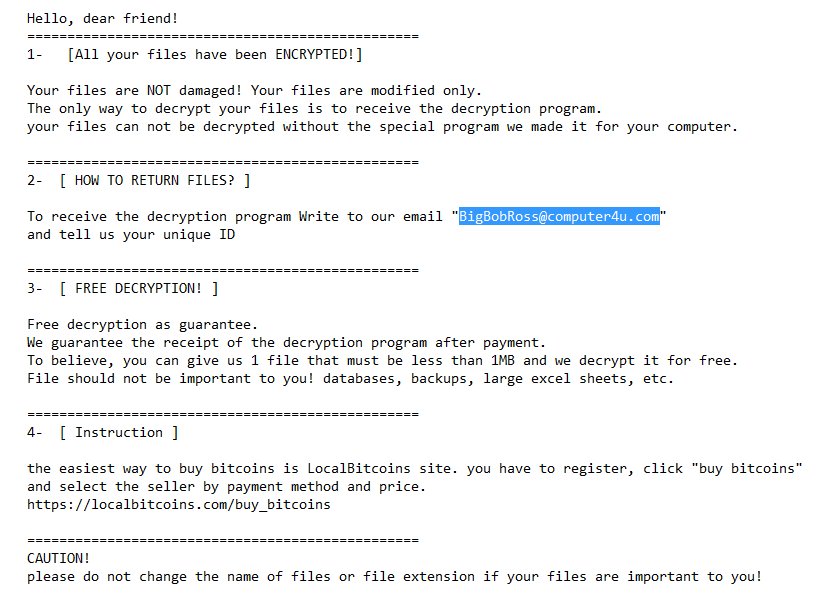
Credit: Emsisoft The ransomware is one of the smaller strains that have silently infected victims for the last two months, while major ransomware operations such as GandCrab, Ryuk, BitPaymer, SamSam or Matrix have all taken the titles. Emsisoft security researcher Michael Gillespie told that the first sighting of BigBobRoss took place on January 14, when victims tried to identify ransomware through ID-Ransomware, a service built years ago by Gilespie, to help victims identify the names of their systems. Gillespie said he received 35 entries from users in six countries later identified as victims of BigBobRoss. However, not all victims know how to use this service, so that the number of victims infected could be much higher. It is not clear how the BigBobRoss crew works to distribute the ransomware or to infect victims when they write. “At least a victim on BleepingComputer said that a server was hacked, but unfortunately I haven’t heard anything else from victims about the vector of the infection,” Gillespie said. In addition to the service ID-Ransomware, victims can easily determine if the BigBobRoss ransomware has been infected with a few visual queues. Firstly, when a victim is infected, most of its files will be encrypted and prepended with the file extension “.obfuscated.” For instance, image.png becomes image.png.obfuscated. The ransom note is stored in a file called “Read Me.txt,” which is integrated as a visual reference below. The name Ransomware comes from the e-mail address found in this ransom note, which hackers are telling victims to reach for more information-BigBobRoss@computer4u.com. Although the.obfuscated file extension is being used, the ransomware-written in C++ using QT-actually doesn’t obscure files and actually encrypt them with an AES-128 ECB algorithm. However, the BigBobRoss decrypters of Avast and Emsisoft work to help victims recover their files. With news this week that officials from Jackson County, Georgia paid $400,000 to recover from a ransomware infection in Ryuk, it is worth remembering the work that some businesses are doing to support ransomware victims, if possible. This is also likely to be the best time to create some of your most important data offline, if only.