Security researchers MalwareHunterTeam found a system in which an intruder created a fake company that offers a free cryptocurrency trading platform called JMT Trader. When downloaded, this software will also infect a victim with a Trojan backdoor.
The Development of a Malware Crypto-Trading Scheme
This program starts with a website designed professionally to promote the JMT Trader software, as shown below. JMT Trader Web Site They also created a Twitter account to promote the page and program to promote the fictitious business. This account is relatively sleepy with its new June tweet. Twitter Account You are brought to the GitHub repository to find Windows and Mac executables for the JMT Trader application if you are attempting to download the software. This site also contains the source code for those who wish to compile it under Linux. This source code doesn’t seem malicious. JMT Trader GitHub Repository Using the JMT Trade software, a client can create different exchange profiles and legally use this to trade cryptocurrency. It software and the above GitHub site are only clones of the legal QT Bitcoin Trader program adopted for that malware activity.
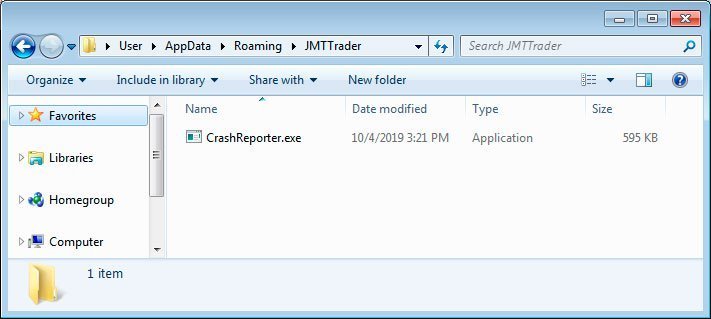
JMT Trader Application Nonetheless, the installer extracts a secondary program called CrashReporter.exe when the JMT Trader has been downloaded, which will save it to the AppData percent \JMTTrader directory. The malware component of this program functions as a backdoor. The malware currently has only 5/69 VirusTotal detections.
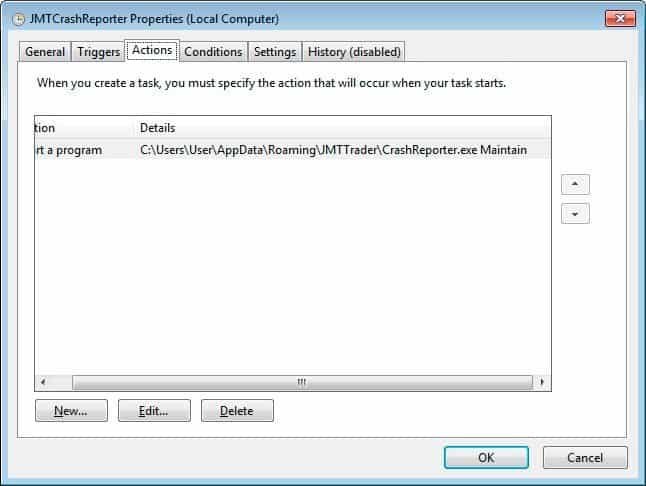
CrashReporter.exe Backdoor A programmed function, called JMTCrashReporter, will be generated, and every time a user logs into the machine the CrashReporter.exe begins.
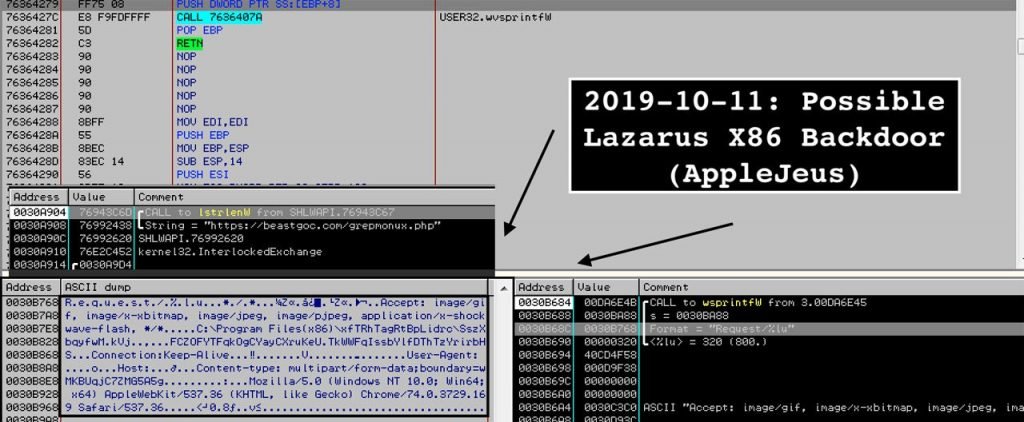
Scheduled Task for CrashReporter According to Vitali Kremez, reverse engineer and author, when the executable CrashReporter.exe begins, it is connected back to a beastgoc[.]com Command & Control database to obtain orders.
Connecting to the C2 Server It is not clear whether the malware would drop any other payload or simply be used to steal cryptocurrency wallets or to swap logins. Whatever the matter, you should be sure to thoroughly check your device for malware, and uninstall the percentage AppData percent \JMTTrader\CrashReporter.exe if it is present, if any users downloaded this software. Victims should then change their passwords in any account exchange.
Possible ties to the party Lazarus APT
MalwareHunterTeam noticed that it was very similar to an earlier cryptotrading malware operation called AppleJeus when examining the scheme. In 2018, Kaspersky found that crypto-monetary exchange is being abused when an employee installs a Trojan-style crypto-monetary trading request. “Kaspersky Lab has been assisting with incident response efforts. While investigating a cryptocurrency exchange attacked by Lazarus, we made an unexpected discovery. The victim had been infected with the help of a trojanized cryptocurrency trading application, which had been recommended to the company over email. It turned out that an unsuspecting employee of the company had willingly downloaded a third-party application from a legitimate looking website and their computer had been infected with malware known as Fallchill, an old tool that Lazarus has recently switched back to. There have been multiple reports on the reappearance of Fallchill, including one from US-CERT.” This attack was linked to the APT group named Lazarus with links to North Korea after further investigation. Although certain aspects have changed, the methods between the JMT Trader scheme seem very similar to Kaspersky’s AppleJeus operations. Both use legitimate, professionally supported cryptotrading applications and both have a secondary malware component system. Although it’s not 100 percent verified that JMT Trader is a Lazarus operation, Seongsu Park, senior security researcher at Kaspersky GReAT, assumes they are linked. Seongsu Tweet This shows you that you must be careful to download programs from the Internet because you never know what you are going to get.