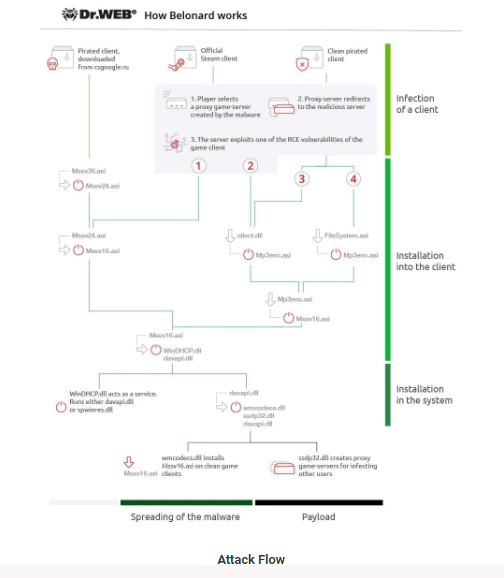
While Counter-Strike 1.6 has nearly 20 years of age, the player base and the game servers still have a strong market. Hosting providers rent game servers monthly with this request and offer other services like promoting a customer’s game server to increase their popularity. Dr Web’s new report explains how a developer uses vulnerabilities of the game customers, the Belonard Trojan botnet and malicious servers to promote their customers ‘ game servers, and to enlist more victims to the botnet. At its peak, this botnet grew so large that around 39 percent of the 5,000 Counter-Strike 1.6 servers were malicious and tried to infect linked players. Start playing togel sgp online to make money easily. “Let us touch upon the process of infecting a client in more detail. A player launches the official Steam client and selects a game server. Upon connecting to a malicious server, it exploits an RCE vulnerability, uploading one of the malicious libraries to a victim’s device. Depending on the type of vulnerability, one of two libraries will be downloaded and executed: client.dll (Trojan.Belonard.1) or Mssv24.asi (Trojan.Belonard.5).” “The Trojan developer succeeded in creating a botnet using this pattern that makes up a substantial part of the CS 1.6 game servers,” Dr. Web’s research says. “Out of some 5,000 servers from an official Steam client, 1,951 were created, according to our analysts, by the Belonard Trojan. This is 39 per cent of all game servers. This network enabled the Trojan Developer to promote other servers for money by adding them to lists of available servers in infected game clients.
” In order to do so, the Belonard botnet used clean clients’ pre-infected clients or remote command vulnerabilities, allowing them to install the Trojan simply via a player on the malicious server. Since the Counter-Strike 1.6 game client is no longer supported, the botnet is potentially a victim of all players in this game. “When a player starts the game, their nickname will change to the address of the website where an infected game client can be downloaded, while the game menu will show a link to the VKontakte CS 1.6 community with more than 11,500 subscribers.” When the Trojan has installed, the Windows service “Windows DHCP Service” will be created and the value of ServiceDLL for loading the C:\Windows\System32\WinDHCP.dll saved Trojan.
Shutting down the Botnet
The trojan then replaces files in the game client that not only promotes the attacker’s website where the game clients infected can be downloaded, but also promotes fake game servers. If a player tries to add one of the servers, it is forwarded to a malicious game server using the RCE vulnerability to infect the victim with the Belonard Trojan. Dr. Web was able to close the domains used by trojans to redirect players to fake game servers in coordination to the REG.ru domain name registrar. This will help prevent the infection of new players. Dr. Web continued to monitor other domains used in the Domain Generation Algorithm (DGA) of the malware, but sinkholes could prevent further infections so far. Sadly, the only way to prevent the recreation of this botnet is to fix the vulnerabilities in the client. Since Counter-Strike 1.6 was the last customer released by Valve, no fix is expected.